This article will focus on a vulnerability in inter-network bridge protocols, which is a big security threat to smart contracts between different blockchains.
Cross bridges are an attractive target for hackers because they often represent a central storage point for the funds that support the “bridge” assets on the receiving blockchain.
What are Internet Bridge Protocols?
Bridges are designed to solve the problem of interoperability between different blockchains. A bridge is a protocol that allows a user to transfer digital assets from one blockchain to another. One of the most famous examples Wormholeis the bridging protocol, which allows users to move cryptocurrencies NFTbetween different smart contract blockchains such as Solana and Ethereum. In February 2022of the year, there was a case when an unknown hacker found an exploit in the smart contract code Wormholethat allowed him to create 120 000 Wrapped Ethereumon Solana (WeETH)without providing the necessary equivalent collateral Ethereum.
To understand why this incident was more serious than a normal hack, we need to know how cross bridges work. Users interact with bridges by sending funds in one asset to the bridge protocol, where the funds are then fixed in a contract. The user is then given the equivalent funds of the parallel asset on the chain to which the protocol is connected. In the case of Wormhole, users typically send ether (ETH)to the protocol, where it is stored as collateral, and issued WeETHto Solana, backed by the collateral locked in the contract Wormholeto Ethereum.
This high-profile hack meant that WeETH$ Solana320 million was not secured within a certain period of time. If Ethereum WeETHwas not secured, this would mean that a number of platforms on the basis of Solanaaccepting WeETHas collateral could become insolvent. We could see users rush to sell their WeETH, causing its value to drop, with major implications for the blockchain Solanaand the vast ecosystem DeFibuilt on top of it, as many of these protocols also rely on WeETHto back issued assets. users. Indeed, last night we saw the price Solanaof 13,5%, which many attribute to fears of a hack.
Jump Trading, the parent company of Wormhole and a major player in the Solana ecosystem, tweeted:
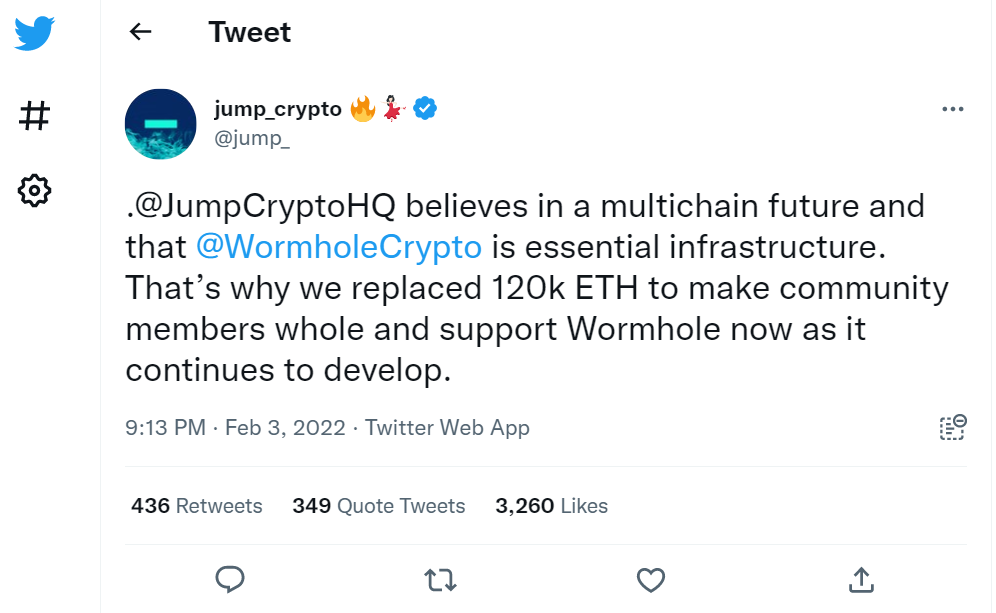
Jump Tradingprovided coins to ETHreplace stolen funds after attempts to pay the hacker a reward for the stolen funds were ignored.
Bridge construction
Bridge designs vary, users typically interact with bridges by sending funds in one asset to the bridge protocol, where the funds are then fixed in a contract. The user is then given the equivalent funds of the parallel asset on the chain to which the protocol is connected. In the case of a wormhole, users typically send ether (ETH)to the protocol, where it is stored as collateral, and released ETHwormhole-wrapped to , backed Solanaby the collateral locked in the wormhole’s contract to Ethereum.
Vulnerable cross bridges
Bridges are an attractive target because they often represent a central storage point for the funds that support “bridge” assets on the host blockchain. Whether these funds are stored in a smart contract or in a centralized custodian, this storage point becomes the target. In addition, efficient bridge design is still an unresolved technical issue, with many new models being developed and tested. These various schemes represent new attack vectors that could be exploited by attackers as best practices improve over time.
Just a few years ago, centralized exchanges were the most common target for hacks in the industry. Today, successful hacks of centralized exchanges are rare. This is because these organizations prioritize their security, and also because hackers are always on the lookout for the latest and most vulnerable services to attack.
While not reliable, a valuable first step to solving problems like this could be extremely rigorous code auditing, which would become the gold standard DeFifor both these build protocols and the investors who evaluate them. Over time, the most reliable and secure smart contracts can serve as templates for developers. Cryptocurrency services, including but not limited to bridges, must invest in security measures and training.
Conclusion:
At the moment, all these modern attacks on bridges account for 69%all the funds stolen in a 2022year. This poses a serious threat to blockchain technology. As more value passes through cross-chain bridges , they become more attractive to hackers.
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/9rDEepQOyaM
Source: https://cryptodeeptools.ru/cross-chain-bridge

