In this article, we will tell you about the most daring and biggest thefts of cryptocurrencies associated with платформой DeFi. Hackers had a big year in 2021 when they stole $3.2 billion worth of cryptocurrencies. But in 2022, the amount of theft of cryptocurrencies reached a historical maximum. In the first three months of this year, hackers have stolen $1.3 billion from exchanges, platforms, and individuals , with a correspondingly disproportionate number of victims платформу DeFi.
What is DeFi ?
DeFi is financial instruments in the form of services and applications built on the blockchain. The main task of decentralized finance is to become an alternative to the banking sector and replace the traditional technologies of the current financial system with open source protocols. That is, open access to decentralized lending and new investment platforms to a large number of people, as well as allow them to receive passive income from cryptocurrency assets.
Nearly 97% of all cryptocurrency stolen in the first three months of 2022 was taken from DeFi protocols, up from 72% in 2021 and just 30% in 2020.
Code exploits are becoming an increasingly common attack vector, but security breaches are here to stay. In the past, crypto-currency hacks were mostly the result of security breaches where hackers gained access to victims’ private keys – the crypto equivalent of pickpocketing. However, for DeFi protocols in particular, the biggest thefts usually come from buggy code. “Code exploits” and “flash loan attacks” — a type of code exploit related to the manipulation of cryptocurrency prices — account for most of the cost.
Most existing DeFi is built on the Ethereum blockchain, and the number of new decentralized finance applications is steadily growing. DeFi uses various technologies developed in the field of blockchain. All of them have applications outside of decentralized finance, but play an important role in the DeFi ecosystem. First of all , DeFi projects are blockchains , distributed ledgers for recording transactions. Currently, most DeFi services run on the Ethereum network due to its capabilities and popularity among developers. However, DeFi activity is also growing on other blockchains. Next come digital assets, i.e. DeFi tokens that represent a value that can be sold or transferred on the blockchain network. “Bitcoin and other cryptocurrencies were the first blockchain-based digital assets.
Code exploits occur for a number of reasons. First, in line with DeFi’s belief in decentralization and transparency, open source development is a staple of DeFi applications. This is an important and generally positive trend: since DeFi protocols move funds without human intervention, users should be able to verify the underlying code in order to trust the protocol. But it also benefits cybercriminals, who can analyze scenarios for vulnerabilities and plan exploits in advance.
Ronin Network
| Victim | Amount stolen (USD) | Service Type | Type of hack | Description |
| Ronin Network | $625 million | DeFi Platform | security breach | The attacker gained access to five of the nine private keys of the transaction validators, and then used this majority to confirm the withdrawal of funds in ETH and USDC. |

Axie Infinity’s Ronin network hit by $625M exploit
The latest crypto hack may be the biggest yet.
Gaming-focused network Ronin posted losses of more than $625 million in USD and Ether (ETH) on Tuesday.
According to a blog post published by the official Substack of the Ronin network , the exploit affected the Ronin validator nodes for Sky Mavis, publishers of the popular game Axie Infinity, and Axie DAO
(March 30, 13:23 UTC): Ronin Hacker unlikely to cash out ‘GDP-sized’ loot, experts say
As seen on Etherscan, the attacker “used compromised private keys to fake withdrawals” from the Ronin bridge across two transactions .
While the Ronin sidechain has nine validators requiring five signatures for withdrawals and is designed to protect against these types of attacks, the blog post notes that “an attacker found a backdoor through our gasless RPC node that they abused to get signature for the Axie DAO validator”.
The blog post estimates the loss at 173,600 Ether and $25.5 million, which is currently over $625 million.
Back in August 2021, a hacker got away with $611 million using the Poly Network ’s cross-chain decentralized finance (DeFi) protocol . The vast majority of funds were returned .
Ronin’s Ethereum address is the new address where ETH was transferred from the Binance exchange a week ago. The Etherscan records show that the attack took place last Wednesday.
Most of the funds remain in the attacker’s address, although 6,250 ETH was transferred to other addresses.
Ronin Bridge and automated market maker Katana (AMM) have been suspended pending investigation.
“We work directly with various government agencies to bring criminals to justice,” the blog notes.
According to CoinGecko, the price of RON , the native token of the Ronin network, fell 27% on the news.
Poly Network
| Poly Network | $612 million | DeFi Platform | Code exploit | The attacker used cross-chain relay contracts to extract Poly Network funds from three different chains: Ethereum, BSC, and Polygon. The attacker eventually returned the stolen funds. Read our full case study . |

Exploit in smart contracts Poly Network
On August 10, 2021, a hitherto unknown attacker stole $612 million worth of cryptocurrencies from the Poly Network DeFi protocol, making it the largest theft from the DeFi protocol. But in an incredible coincidence, the attacker appears to return the funds to Poly Network a day later.
The attacker carried out the heist using an exploit in the smart contracts Poly Network uses to perform cross-chain transactions. Ethereum programmer Kelvin Fiechter has tweeted a detailed account of exactly how the exploit worked if you’d like to know more . The attacker stole funds in the following cryptocurrencies:
- ETH
- WETH
- WBTC
- HIM
- RenBTC
- USDT
- USDC
- COME ON
- SHIB
- FEI
- BNB
- Various BEP-20 Tokens
Poly Network has publicly identified three addresses that we have confirmed are controlled by the attacker:
- Attacker Address 1: 0xC8a65Fadf0e0dDAf421F28FEAb69Bf6E2E589963 (ETH)
- Attacker address 2: 0x0D6e286A7cfD25E0c01fEe9756765D8033B32C71 (BSC)
- Attacker address 3: 0x5dc3603C9D42Ff184153a8a9094a73d461663214 (POLYGON)
Below, we will share some notes on how the attack was carried out, how much the attacker has already returned to Poly Network, and the current address balances of the attackers.
Notes on initial cash flows
We discovered some interesting facts while analyzing the initial movements of the stolen funds by the attacker. Check out the Chainalysis Reactor chart below , which shows that attacker address 1 received 2,857.59 ETH worth $274,461,628.15 from Poly Network in the initial theft.

We can see that the day before, the attacker withdrew 0.47 ETH from Hoo.com, which was used to pay gas fees for transactions related to the hack. Additionally, the attacker apparently sent 13.37 ETH to a user known as Hanashiro.eth, who sent the attacker an Ether transaction with a message warning them that the USDT stolen from the Poly Network was frozen.

Apparently, the attacker Poly Network is willing to pay good money for reliable information.
The attacker also stole 673,227 DAI and 96,389,444 USDC from Poly Network. The attacker sent the full amounts of both to the Curve DeFi protocol to mint 95,269,796 3CRV tokens. Within an hour, the attacker burned those 3CRV tokens to get 96,942,061 DAI.

We suspect the attacker’s goal was to swap their holdings of a centralized USDC stablecoin for a decentralized one such as DAI in order to reduce the possibility of a freeze on funds.
Return of stolen funds and current balances
Surprisingly, the attacker now appears to be in the process of returning the stolen funds to Poly Network at their request . Since August 11, they have started sending funds back to three Poly Network addresses:
- 0x71Fb9dB587F6d47Ac8192Cd76110E05B8fd2142f
- 0xEEBb0c4a5017bEd8079B88F35528eF2c722b31fc
- 0xA4b291Ed1220310d3120f515B5B7AccaecD66F17
As of 12:45 pm ET on August 12, the attacker recovered all of the stolen funds, except for the frozen $33.4 million. In total, the attacker returned $578.6 million worth of cryptocurrencies out of the $612 million originally stolen.
- POLYGON USDC
- Binance-Peg BTCB
- Binance-Peg BUSD
- Binance-Peg USDC
- FEI
- SHIB
- Binance-Peg ETH
- BNB
- RenBTC
During this process, the attacker contacted the Poly Network via an ether transaction note , stating their intention to start by returning the altcoins and asking if their stolen USDT could be unlocked in exchange for the return of the stolen USDC.

This may be a ploy to get away with unstolen USDT, but so far there is nothing to indicate that the attacker will not continue to return the stolen funds.
Previously, the hacker had also asked Poly Network to create a multisig wallet for him so that he could continue to return funds, and asked Poly to start sending funds returned so far to affected users.

As of 10:00 AM ET, August 11, 2021, the three attackers’ addresses hold the following balances:
Attacker address 1: 0xC8a65Fadf0e0dDAf421F28FEAb69Bf6E2E589963 .
- USDT – $33,431,234.90
Attacker address 2: 0x0D6e286A7cfD25E0c01fEe9756765D8033B32C71 .
- This address is now empty.
Attacker address 3: 0x5dc3603C9D42Ff184153a8a9094a73d461663214 .
- This address is now empty.
Cryptocurrency security firm Slowmist claims to have identified the intruder’s mailbox, IP address, and device fingerprints, suggesting they may be close to identifying them, but we have no information to confirm this at this time. For their part, the attacker rejects the possibility of being identified in the Q&A they conduct through the Ether transaction notes, where they also explain some of their motives for hacking the Poly Network.
The Poly Network hack and the subsequent refund shows that it is becoming increasingly difficult to carry out large-scale theft of cryptocurrencies. This may seem counterintuitive given that this $600 million theft represents the biggest DeFi hack of all time, and that the rapidly growing DeFi ecosystem is uniquely vulnerable to hacks. However, stealing cryptocurrencies is more difficult than stealing fiat funds. This is partly due to the inherent transparency of blockchains. While criminally obtained fiat currency can be moved through shady bank accounts and authorities rely on subpoenas and the cooperation of financial institutions to trace its path, anyone in the world can view cryptocurrency transactions made on public blockchains.
A growing active cryptocurrency community is constantly increasing the transparency of cryptocurrencies. Minutes after the hack, crypto Twitter was flooded with updates from countless industry operators, reporters and anonymous investigators tracking the attacker’s funds. It would be virtually impossible for an attacker to transfer funds anywhere without someone broadcasting them. This paints a promising picture for future responses to the cryptocurrency hack. With the inherent transparency of blockchains and industry-wide scrutiny, how can any cryptocurrency hacker expect to escape with a large cache of stolen funds? In most cases, the best they could hope for was to avoid capture as the funds are frozen in a blacklisted private wallet.
While we certainly don’t expect every cryptocurrency hack to end with the attacker recovering the stolen funds, in this case, it looks like Poly Network will get their money back and also learned about an important vulnerability that their team can now fix. Ultimately, the ecosystem will be stronger for this. All addresses associated with the Poly Network hack are now flagged in our products. We will continue to monitor the movement of stolen funds and report any material changes.
Wormhole
| Wormhole | $320 million | DeFi Platform | Code exploit | The attacker manipulated the Solana<->Ethereum Wormhole cross-chain bridge into believing that 120,000 ETH had been deposited, allowing them to mint whETH (Wormhole ETH) of equivalent value on Solana. |

The Wormhole network has been used to steal 120,000 wrapped ETH (wETH), which is valued at around $320 million at current Ethereum prices.
News that the Wormhole protocol had been compromised came on February 3, when members of the crypto community alerted their peers on social media that a significant amount of ETH had been leaked from the bridge.
A few hours later, the platform confirmed that the attack had taken place and that the Ethereum-Solana cross-chain bridge had been used.
“The wormhole network was used to receive 120,000 wETH,” the Wormhole Twitter account said in an announcement . The firm went on to add that “ETH will be added over the next hours to provide wETH 1:1 support,” but did not explain where the additional funds would come from.
BitMart
| BitMart | $196 million | Exchange | security breach | The attacker stole the private key that compromised two BitMart hot wallets. |

Cryptocurrency exchange BitMart hacked, losses estimated at $196 million
BitMart’s CEO has confirmed what the company calls a “security breach”.
The latest centralized exchange hack may be one of the most devastating to date, as BitMart lost $196 million in various cryptocurrencies.
A tweet by analytics firm PeckShield first drew attention to the alleged hack on Saturday night. One of the BitMart addresses is currently showing a steady outflow of its entire balance of tokens, some of which are worth tens of millions of dollars, to an address that Etherscan currently labels as “BitMart Hacker.”
In a subsequent tweet, PeckShield estimated losses of $100 million in various cryptocurrencies on the Ethereum blockchain and $96 million in Binance Smart Chain.
The hacker systematically used the 1inch decentralized exchange (DEX) aggregator to exchange stolen assets for cryptocurrency ether (ETH) and used a secondary address to deposit ETH into the Tornado Cash privacy mixer , making it difficult to trace the hacked funds.
On the official Telegram channel, BitMart initially claimed that the outflows were normal withdrawals, calling reports of the hack “fake news.”
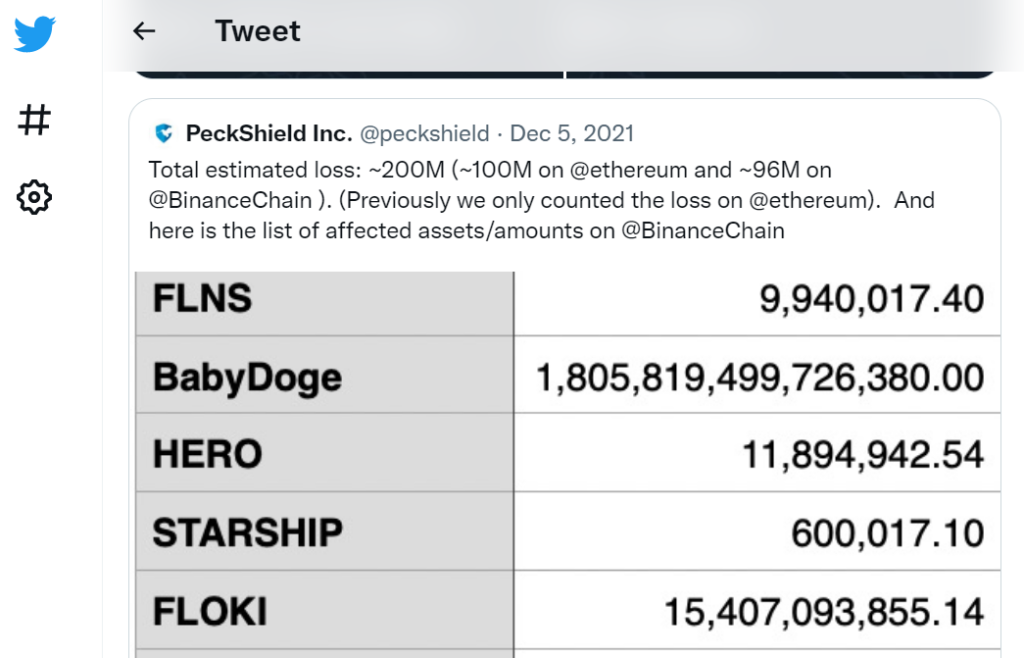
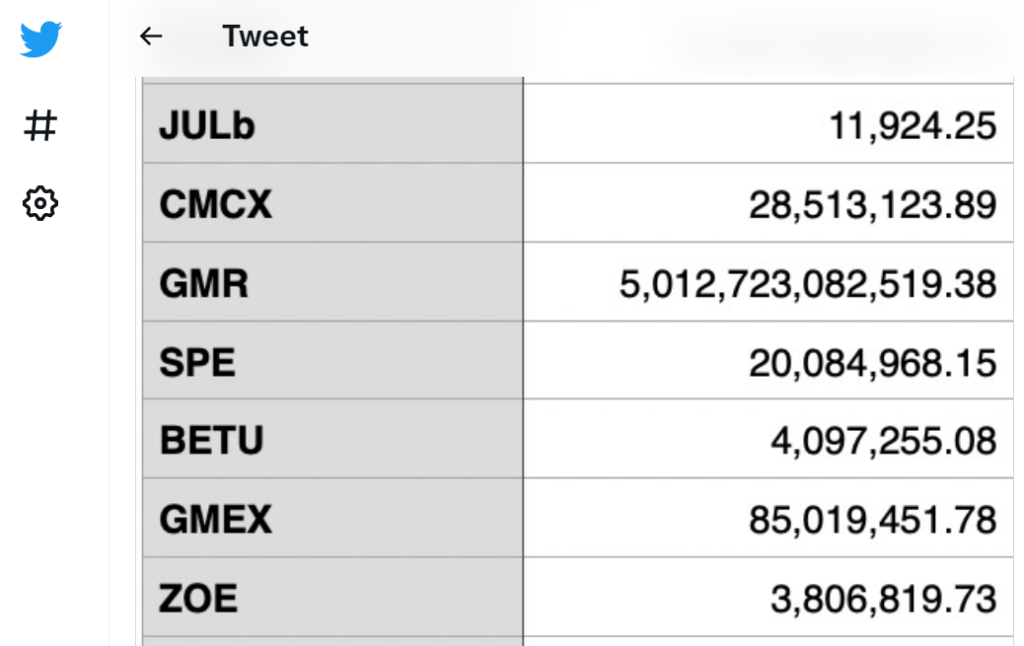
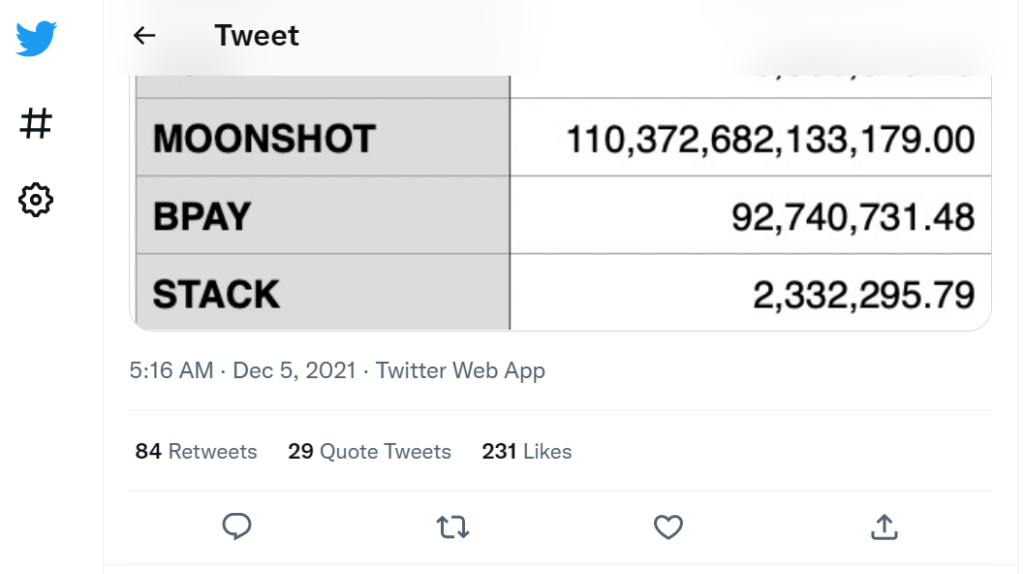
https://twitter.com/peckshield/status/1467316799977193476Hours later, however, BitMart CEO Sheldon Xia confirmed that the outflow of funds was indeed a hack resulting from a “security breach.”
1/3 We have discovered a large scale security breach involving one of our ETH hot wallets and one of our BSC hot wallets. At the moment we are still finalizing the possible methods used. The hackers were able to steal about $150 million worth of assets. — Sheldon Xia (@sheldonbitmart)
The $196 million loss makes this one of the most devastating centralized exchange hacks to date.
BadgerDAO
| BadgerDAO | $150 million | DeFi Platform | security breach | The attacker used a compromised Cloudflare API key to periodically inject malicious scripts into the Badger app. The scripts intercepted transactions and prompted users to allow a foreign account to work with their ERC-20 tokens. Once approved, the attacker siphoned off funds from users’ wallets. |

Investigators believe that an unauthorized API key allowed malicious code to be used to set a user’s Web3 permission on the attacker’s wallet
On December 2, 2021, a series of unauthorized transactions took place , causing Badger users to lose funds. Following the exploit, Badger engineers worked with cybersecurity firm Mandiant to investigate the incident and produced the following initial report.
Badger currently believes that the December 2, 2021, publicly reported phishing incident was the result of a maliciously injected snippet provided by Cloudflare Workers. Cloudflare Workers is an interface for running scripts that work with web traffic and modify it as it passes through Cloudflare’s proxies. The attacker deployed a working script using a compromised API key that was created without the knowledge or permission of Badger engineers. The attackers used this API access to periodically inject malicious code into the Badger application in a way that affected only a subset of the user base.
Event chain
Badger appreciates our community’s patience as we figure out how to balance our commitment to transparency with the fact that this is still an ongoing investigation with rapidly changing information. We are currently sharing the following sequence of events to help protect our community and help others who may experience similar attacks.
- In late September, users on the Cloudflare Community Support Forum reported that unauthorized users were able to create accounts and could also create and view (global) API keys (which cannot be deleted or deactivated) before email verification was complete (see Cloudflare Forum). post ). It was noted that the attacker could then wait for the email to be verified and the account creation to complete before gaining access to the API.
- After examining Cloudflare logs after the exploit, Badger discovered unauthorized account creation and API key generation for three Badger accounts; two at the end of August, one at the beginning of September.
- In mid-September, Badger unknowingly ended up creating an account for one of these three compromised accounts that were used for legitimate Cloudflare management activities. The UI didn’t make it obvious that an account had already been created and an API key was generated accordingly.
- On November 10, the attacker began using his API access to inject malicious scripts through Cloudflare Workers into the app.badger.com HTML code . The script intercepted web3 transactions and prompted users to allow the use of an external address to work with ERC-20 tokens in their wallet. On November 20, the first malicious approval on the network was made for the exploiter’s wallet.
- The attacker used several anti-detection methods in his attack. They applied and removed the script intermittently throughout November, often for very short periods of time. The attacker also only targeted wallets with a certain balance and explicitly avoided targeting registered Dev Multisig signers. Finally, the attacker accessed the API from multiple proxy and VPN IP addresses and modified the script for each deployment so that each had a unique hash that displayed static indicators of limited value.
- The Badger community reported a major suspicious transaction via Discord on December 2nd.
- Badger immediately suspended most operations on the vault within 30 minutes of the warning. Several old contracts with a single unavailable guardian were put on hold after about 15 hours.
- Following this incident, Cloudflare API keys were swapped, passwords changed, and MFA was transferred after the incident was discovered.
Since this exploit involved Web 2 vectors that are unusual for DeFi attacks, we will provide a brief breakdown of the Web 2 events that occurred and a full Web 3 breakdown that complies with DeFi reporting standards.
Web2 event log
Badger provides the following information to help other people identify a similar Web2 hack.
Here is what our Cloudflare audit logs look like for one of the hacked accounts:
The earliest evidence currently available that an attacker attempted to take over the account dates back to August 20, 2021.
Judging by the responses on the Cloudflare forum, the vulnerability was patched around September 29th.
Here’s what the Badger app looked like with the injected code:
Archived version of the Badger app with embedded code
Badger is currently editing the malicious scripts from the summary below while the investigation continues.
On November 10, 2021, here is the first example of malicious activity.
Web3: Network Events
Mitigation Steps
Around 2:05 AM UTC on December 2, 2021, Badger was alerted to suspicious activity on the platform. The attack was noticed by a member of the community when around 900 BTC was removed from the Yearn wBTC vault .
After a quick investigation, the issue was marked as high priority and urgent. At 3:14 AM UTC, Badger began suspending all storage and strategy contracts.
Under BIP -33 , addresses approved in a trustee agreement have the ability to suspend agreements. The way the pause function of these contracts works is to block any deposit, withdrawal, transfer to ERC20 vaults, withdrawal from strategies, and any minting/redemption of ibBTC until the resume pause function is called on them. Resuming the pause is limited to Dev Multisig and requires management approval. Eight old strategies and one storage also require a temporary lock to resume the pause.
Most of the contracts were suspended by 3:30 am UTC. Some older stores (namely bcrvRenBTC, bcrvSBTC, bcrvTBTC, bBADGER, bharvestcrvRenBTC and buniWbtcBadger) do not have a pause feature in the store contract. However, their strategies have been put on hold to prevent withdrawals. At the time, Badger engineers could not access the bBADGER, bharvestcrvRenBTC, and buniWbtcBadger strategy keeper account. Further investigation revealed that the strategist who helped come up with this smart contract idea also had suspend capabilities, and ultimately the strategists that suspended were able to suspend the strategies using the strategist’s account.
A list of all suspended txs can be found here . As soon as the storages were paused, the transferFrom calls on the exploiter started to fail.
The charts below show Badger Sett movement stopping after a pause. (Note: Y-axis shows the original number of Badger Sett tokens)
All Setts except bBADGER, bharvestcrvRenBTC and buniWbtcBadger:
Below is a graph showing the movement of all Badger Sett tokens, including late-pause tokens.
It is worth noting that the last malicious removal from the unsecured vaults occurred at 4:57 am UTC. All withdrawals that occurred after that and before the suspension of the last strategy were made by ordinary users.
It is also worth mentioning that the attacker was able to compromise non-Sett tokens such as BADGER, wBTC, CVX, and cvxCRV and was able to liquidate them after Badger introduced pauses.
Performing an attack
Through the Web2 intrusion, the attacker was able to gain approval of the ERC20 token from Badger users through the user interface. The hacker tricked users into signing assertion token or permission escalation calls, allowing the primary EOA exploiter account (0x1fcdb04d0c5364fbd92c73ca8af9baa72c269107) to spend funds.
After a phishing series of approvals , the funding account sent 8 ETH to the exploiter account to launch a series of TransferFrom calls to the approved user tokens. This allowed the attacker to transfer funds on behalf of users to other accounts, which then liquidated the funds and exited through the Badger Bridge to BTC.
Parties involved
Badger is actively monitoring all incident-related funds and related information is available below:
Destination addresses:
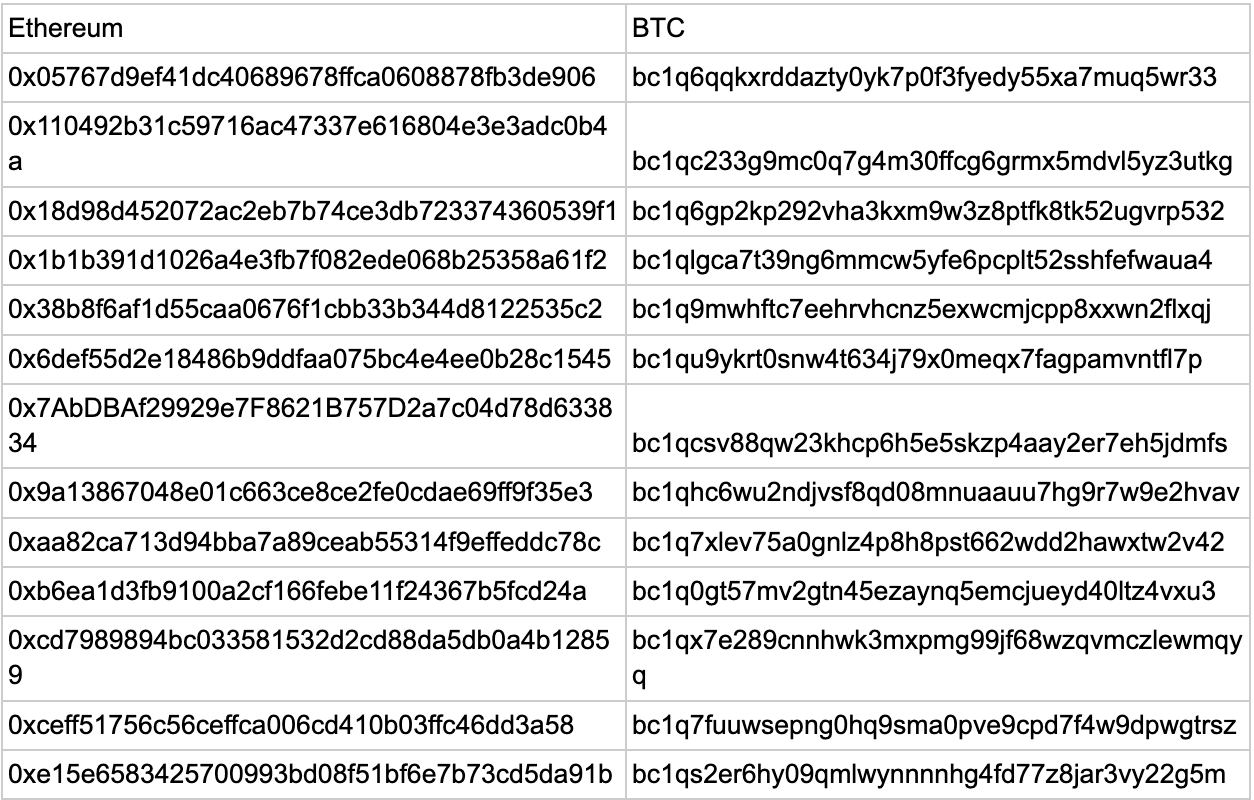
Protocol impact (stolen funds)
Impact on underlying assets:
Note. Estimated USD prices are based on fixed prices taken since the start of the collection script (December 2, 2021). They should be taken as an indication, not as an absolute. A detailed breakdown of the tokens can be found here .
Plan after the incident
The Badger Cloudflare account has had its password updated, MFA changed, and all API keys either removed or updated where possible.
Badger confirmed that the exploit was patched on Cloudflare’s side. New accounts are no longer allowed to view API keys until the email address has been verified.
The way forward
Badger is currently evaluating and working on a plan to implement the following potential improvement ideas:
- Revise the emergency functionality in all smart contracts to ensure it is universal and automate the “suspend all” functionality to reduce Badger’s emergency break time from 15 minutes to 2-3 minutes.
- Complete third-party audits of the entire web2 and web3 infrastructure before restarting the protocol.
- Badger could potentially fund a hack race to create detection technology to monitor all smart contracts for unexpected assertions, or to automatically generate alerts for heuristic changes in how calls are made.
- Add a minified IPFS-deployed trust version for the Badger app.
- Create public repositories so people can build from source.
- Badger could educate the community about the importance of vigilance and set up new channels to make sure changes in the behavior of community members are quickly heard and analyzed.
- Badger can create monitoring tools to compare the site served by all routes to https://app.badger.com and match them against a locally built SPA to ensure no code injection in the future.
Note for DeFi developers and security researchers:
While the report is preliminary and does not include all of the information from its investigation, Badger would be more than happy to discuss some additional findings and share more information with the DeFi and Infosec community as much as possible given the ongoing investigation.
| Undisclosed | $145 million | Private | Other is waste | An employee allegedly transferred funds to a personal account when the company attempted to transfer funds between financial accounts. |
Venus
| Venus | $145 million | DeFi Platform | Code exploit | The attacker manipulated the price of XVS, the Venus Protocol governance token, to borrow more BTC and ETH than the actual value of XVS. When the price of the governance token declined and users of the protocol defaulted on their loans, Venus was left with $145 million in debt. |

| Charts | $139 million | DeFi Platform | Leakage of private keys | An unknown member of the BXH tech team allegedly leaked the admin private key. |

$139 million BXH exchange hack resulted in admin key leak
According to the CEO, the break-in could have been the work of one of BXH’s employees.
The hack of Boy X Highspeed (BXH), a decentralized cross-chain exchange that drained $139 million, was likely the result of an admin key leak and possibly internal work, CEO Neo Wang told CoinDesk.
- Based on consultation with an external security team, BXH says the hacker was likely able to break into the exchange’s Binance Smart Chain address after obtaining the admin’s private key, Wang said.
- According to Wang, the hacker either hacked into the key owner’s computer or could have been one of BXH’s technical staff. According to the CEO, the team is looking into the possibility that a hacker installed a virus on BXH’s own website, which was clicked on by an administrator, giving the attacker access to his computer and eventually a key.
- BXH announced the hack on Twitter on Sunday. According to the team, the funds of BXH users in Ethereum, Huobi ECO Chain and OKEx OEC are safe. BXH has suspended withdrawals until the issue is resolved.
- The inner working theory is supported by findings indicating that the attacker was based in China, where the CEO says most of BXH’s tech team is based.
- Wang attributed these findings to PeckShield, a blockchain security company that is working on a case with BXH. He said he was confident that, with the support of PeckShield and the Chinese authorities, the hacker would be tracked down.
- If the hacker is not found or the money is not returned, Wang said, BXH will take full responsibility for the incident and develop a plan to repay the debt.
- BXH is offering a $1 million reward to all teams that help recover the funds and will give the hacker an indefinite reward if the money is returned.
- PeckShield confirmed the leaked admin key theory on Twitter early Monday morning, without providing details.
- According to the CEO, BXH has also filed a lawsuit with the China Network Security Police, a special service that investigates digital crimes.
- The hack is one of several attacks on DeFi projects in the past couple of months. Just days before the BXH attack, Cream Finance suffered a $130 million loss. August saw the biggest hack in DeFi history when the Poly Network internet protocol lost $600 million, which was eventually recovered.
Cream Finance
| Cream Finance | $130 million | DeFi Platform | Flash Loan | The attacker initiated a series of express loans to mint about $1.5M in crYUSD. The attacker then used the Cream PriceOracleProxy feature to artificially increase the value of his crYUSD to ~$3 billion. $2 billion of this amount was withdrawn to pay off the attacker’s outstanding express loans, while the remaining $1 billion was used to drain all of Cream’s available lending assets ($130 million). |

Hackers stole $130 million from Cream Finance
Hackers have stolen about $130 million worth of cryptocurrency assets from Cream Finance, a decentralized finance (DeFi) platform that allows users to lend and speculate on cryptocurrency price fluctuations.
The incident, discovered earlier today by blockchain security firms PeckShield and SlowMist , was confirmed by the Cream Finance team earlier today.
Attackers are believed to have discovered a vulnerability in the platform’s lending system called flash lending and used it to steal all of Cream’s assets and tokens running on the Ethereum blockchain, according to blockchain security company BlockSec, which also posted an explanation of the security vulnerability on Twitter. earlier today.
Our initial analysis of the Cream Finance attack: https://t.co/TysI7fjyPU @Mudit__Gupta @bantg @CreamdotFinance pic.twitter.com/wScUvizBtX — BlockSec (@BlockSecTeam)
A breakdown of the stolen funds is available below, courtesy of the SlowMist team.
About six hours after the attack, Cream Finance said it had fixed the bug used in the hack using the Yearn cryptocurrency platform.
Even if the attacker’s original wallet used to steal the large amount of funds has been identified , the funds have already been moved to new accounts and there is a small chance that the stolen cryptocurrency can be tracked and returned to vault. Platform.
Today’s hack marks Cream Finance’s third hack this year, after the company lost $37 million in February and another $29 million in August .
All of the attacks were exploits for flash loans, which is a common hack for most DeFi platforms over the past two years.
DeFi-related hacks accounted for 76% of all major hacks in 2021, and users have lost more than $474 million in attacks on DeFi platforms this year, according to an August report by CipherTrace .
Similarly, DeFi hacks also accounted for 21% of all cryptocurrency hacks and theft of funds in 2020 after being almost non-existent a year earlier in 2019, according to the same CipherTrace report last year .
The Cream heist was also the second-biggest cryptocurrency hack this year after DeFi platform Poly Network lost $600 million in August . However, the man behind the Poly hack returned all of the stolen funds two weeks later, promising that the company would not press charges.
Vulcan Forged
| Vulcan Forged | $140 million | DeFi Platform | security breach | The attacker gained access to the private keys of 96 addresses and sent their contents to wallets controlled by the hacker. |

Vulcan Forged Play-to-Earn gaming platform refunds users after $140M hack
PYR token prices fell 34% to $21 on Monday following news of the hack.
NFT platform Vulcan Forged said on Tuesday that it returned $140 million worth of PYR tokens to nearly all investors a day after the platform was hacked.
- Built on top of the Polygon network, the platform offers over six blockchain games, a decentralized exchange, and a non- fungible token marketplace.
- “All My Forge wallets are protected. Few need a PYR refund,” the developers tweeted. They said buybacks and token burns—the mechanisms by which projects buy tokens on the open market and send tokens to the “burn” address, respectively—would take place in the coming days.
Update: Most of the PYR has been returned to the affected wallets from the VF treasury.We have isolated tokens stolen from all CEX exchanges. We’re working to identify the tracks.The 100% decentralized solution was perhaps the beacon of light in this.All development is ongoing. — Vulcan Forged (@VulcanForged)
- All returns were made from the treasury of Vulcan Forged, a fund that crypto projects use to save money in case of crises. Refunds were made in PYR and LAVA tokens starting late Monday evening and continuing until Tuesday morning.
- PYR tokens fell 34% to $21 on Monday following news of the hack. PYR recovered slightly to $24 during European hours on Monday and dropped to $21.15 at press time.
- The hackers stole 4.5 million PYR – almost 9% of the total supply of tokens – worth $140 million at the time, as well as a relatively small amount of ether (ETH) and landfill (MATIC).
- Hackers have taken over 96 private keys belonging to some of Vulcan Forged’s biggest users. Private keys are digital signatures that prove ownership of the base address, allowing only their owners to move funds from those addresses.
Conclusion:
This article is created thanks to the “Chainalysis” research provided in the Cryptocrime Report over the 2021 - 2022years. Our personal observation makes it clear that an overall stricter approach to security is needed for all “DeFi” platforms , as the funds locked up have reached a critical point, to a higher all-time high of $256 billion .
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/2bt71AB2Amw
Source: https://cryptodeeptools.ru/defi-attacks

