The rise of fake cryptocurrency apps and how to avoid them. Scammers are using fake crypto apps to steal funds from investors. Some malicious apps find their way into official app stores.
And, according to the latest fraud report, fraudsters are using fake crypto apps to steal money from unsuspecting crypto investors. It highlights that American investors have lost approximately $42.7 million to swindlers through fake apps.
The schemes reportedly take advantage of heightened interest in cryptocurrencies, especially during bull market runs, to beguile crypto users.
How fake crypto app scammers lure users
Fake crypto app scammers use myriad techniques to entice investors. The following is a breakdown of some of them.
Social engineering schemes
Some fake crypto app scammer networks use social engineering strategies to entice victims.
In many cases, the fraudsters befriend the victims through social platforms such as dating sites and then trick them into downloading apps that appear to be functional cryptocurrency trading apps.
The scammers then convince users to transfer funds to the app. The funds are, however, “locked in” once the transfer is made, and the victims are never allowed to withdraw money.
In some cases, the scammers lure victims using outlandish high-yield claims. The ruse comes to an end when the victims realize that they can’t redeem their funds.
Speaking to Cointelegraph earlier this week, Rick Holland, chief information security officer of Digital Shadows — a digital risk protection firm — underscored that social engineering remains a top strategy among crooks because it requires minimal effort.
“Relying upon the tried-and-true method of social engineering is far more practical and lucrative,” he said.
The cybersecurity manager added that social engineering makes it easy for scammers to target high-net-worth individuals.
Context: Bob ( fake name, real person) received a text claiming to be from his exchange. The message states that due to the recent ban on crypto in China, all users must withdraw their funds to a defi wallet. The text also included a link to the wallet where Bob can transfer his funds. After downloading the wallet, Bob removed all of his funds from the exchange. More than $10 million in ERC20-USDT were transferred. Little did Bob know that he had just become the victim of a phishing scam. Bob reached out to us for help recovering his funds.
Bob wasn’t the first person to contact us regarding these scams. Scams are becoming more common as interest in cryptocurrency grows. According to data from our MistTrack service, more than 60% of all reported hacks were related to fake wallets.
There are several ways to protect yourself against phishing attacks:
- Never click on any link from an unknown source, even if it appears legitimate. Scammers frequently send emails or texts containing links to a fake wallet.
- Always go to the original website rather than clicking on sponsored ads. Scammers often purchase ad space on search engines to promote their counterfeit website that often appears genuine.
- Scammers will regularly message you pretending to help. After gaining your trust, they will send you a link to download their app and transfer funds to it. They will often fabricate why you cannot withdraw funds unless you deposit additional funds into it.

Many who fall victim to these scams never receive their money back.
Scammers would often pose as support from Metamask. They would pretend to help anyone currently having difficulties using Metamask. After gaining their trust, they would send over a link asking the victim to input their seed phase. Metamask will NEVER ask for your seed phrase or private key. This is what a fake Metamask wallet might look like.


In-depth analysis
Our team begins to analyze and research the information provided by these victims. According to our ongoing investigation, tens of thousands of victims had their assets stolen from these phishing scams. So far, the total amount stolen exceeds $1.3 billion. These are the only funds reported to SlowMist, and we only counted ETH, BTC, TRX, ERC20-USDT, and TRC20-USDT.

The graph below depicts the number of reported cases to us during November.

One victim provided us with the Tron address of the scammer. Using MistTrack, our team was able to track down and analyze the scammer’s address. It showed an additional 14 addresses that had transferred funds to this address. We can assume that these addresses also fell victims to this phishing scam. In total, the scammer was able to walk away with over $250,000 in Trc20-USDT. Which they later distributed to various Binance accounts.

We followed one of these Binance accounts and discovered it had over $600,000 in TRC20 — USDT. Imagine the total amount stolen if this was just one of the addresses the scammer uses.
As we investigated further into this account, we discovered more illegal activity associated with it. According to our AML(anti-money laundering) software, a BTC address associated with this account (32q…fia) was used for extortion. Through the investigation of this address, we concluded that these phishing schemes were not isolated events but rather part of a larger global scale.

Furthermore, our research indicates that the scammer will frequently transfer portions of the funds to multiple exchanges and to another scammer wallet with a significant amount of transactions to confuse our analysis.

Recognizable brand names
Some fake crypto app scammers have resorted to using recognizable brand names to push fake apps because of the trust and authority that they wield.
In one case highlighted in the latest crypto crime report, cybercriminals posing as YiBit employees recently hoodwinked investors out of some $5.5 million after convincing them to download a bogus YiBit crypto trading app.
Unbeknown to the investors, the actual YiBit crypto exchange firm ceased operations in 2018. Fund transfers made to the fake app were stolen.
In another case outlined in the report, phishers using the Supay brand name, which is associated with an Australian crypto company, swindled 28 investors out of millions of dollars. The ploy, which ran between Nov. 1 and Nov. 26, caused $3.7 million in losses.
Such schemes have been going on for years, but many incidences go unreported due to the lack of proper recourse channels, especially in jurisdictions that shun cryptocurrencies.
Besides the U.S., investigations in other major jurisdictions such as India have in the recent past uncovered elaborate fake crypto app schemes.
According to a report published by the CloudSEK cybersecurity company in June, a newly discovered fake crypto app scheme involving numerous cloned apps and domains caused Indian investors to lose at least $128 million.
Distributing fake apps through official app stores
Fake crypto app scammers sometimes use official app stores to distribute dodgy applications.
Some of the apps are designed to collect user credentials that are then used to unlock crypto accounts on corresponding official platforms. Others claim to offer secure wallet solutions that can be used to store a diverse range of cryptocurrencies but pilfer funds once a deposit is made.
While platforms such as Google Play Store constantly review apps for integrity issues, it is still possible for some fake apps to slip through the cracks.
One of the latest methods used by scammers to accomplish this is registering as app developers on popular mobile app stores such as the Apple App Store and Google Play Store and then uploading legitimate-looking apps.
In 2021, a fake Trezor app masquerading as a wallet created by SatoshiLabs used this strategy to get published on both Apple App Store and Google Play Store. The app claimed to provide users with direct online access to their Trezor hardware wallets without needing to connect their Trezor dongle to a computer.
Victims who downloaded the fake Trezor app were obligated to submit their wallet seed phrase to start using the service. A seed phrase is a string of words that can be used to access a cryptocurrency wallet on the blockchain.
The submitted details allowed the thieves behind the fake app to loot user funds.
According to a statement provided by Apple, the fake Trezor app was published on its store through a deceptive bait-and-switch maneuver. The app developers are alleged to have initially submitted the app as a cryptography application designed to encrypt files but later on converted it to a cryptocurrency wallet app. Apple said that it was not aware of the change until users reported it.
Speaking to Cointelegraph earlier this week, Chris Kline, co-founder of Bitcoin IRA — a crypto retirement investment service — said that despite such incidents, major tech companies in the space were resolute in fighting fake crypto apps because of the potential damage to their integrity. He said: “Tech companies are always looking for better education and security for their users. The most reputable players today put security at the forefront of their roadmaps. Users need reassurance that their digital assets are safe and providers are keeping security top of mind.”
That said, the fake app problem is more prevalent in non-official app stores.
Cryptocurrency is risky enough without having to worry about scams. No matter which one you choose, you will deal with volatile values. Throw in some crooks, and the risk goes up exponentially.
Social media is a goldmine for scammers to find new victims. Now, fake crypto ads are circulating on Facebook and other platforms. The ads use images of well-known industry leaders to lure people into buying crypto that doesn’t exist.
Cybersecurity researchers recently found 40 copycat sites designed to look like legitimate crypto services. The sites advertise crypto wallet apps that are anything but legitimate. Keep reading to find out the risks and protect your finances.
Watch your wallet
Cryptocurrency wallets are physical or digital storage devices for your cryptocurrency. The wallets themselves hold public and private keys, which give you access to your crypto.
How to spot a fake crypto app
Fake cryptocurrency apps are designed to resemble legitimate apps as closely as possible. As a crypto investor, one should be able to discern between legitimate and fake apps to avoid unnecessary losses.
The following is a breakdown of some of the things to look out for when trying to ascertain the authenticity of a mobile crypto application.
Evidence shows that a crook is recruiting partners to distribute these bad apps via telemarketing, social media, advertisement, SMS, third-party channels, fake websites and more.
ESET researchers also uncovered malicious wallets being distributed via legitimate Chinese websites, with articles containing links to fake wallet apps. The posts used real wallet names such as Coinbase, imToken, Bitpie, MetaMask, TokenPocket, OneKey and Trust Wallet but led to copycat websites.
A thief used another legitimate Chinese website to post an article about Beijing’s crypto ban. The author included a list of genuine crypto wallets to get around the ban, along with links to bogus websites with download links for fake apps.
Different effects on iOS and Android
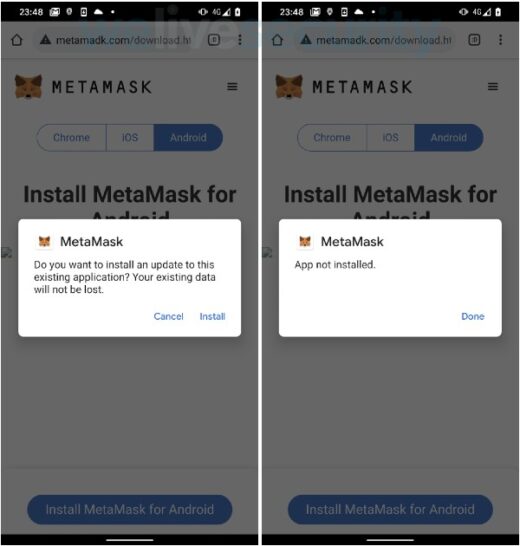
The malware works differently depending on your operating system. The fake Android wallet apps target new crypto users who do not have a legitimate wallet app installed on their devices.
If you already have an official wallet app, the malicious one won’t be installed due to Android security measures, which don’t let you replace an original app with one that isn’t legitimate.
The copycat websites let Android users download the malicious apps from their servers even if they tap on the “Get it on Google Play” button. Following that, the app needs to be installed manually.

When it comes to iOS, multiple versions of an app can be installed simultaneously. But due to Apple’s stricter screening process, you won’t find these malicious apps in the App Store. So if you are an Apple user, you’d have to install the malicious apps from a third-party store or click on malicious links found on places like social media.
The websites for these apps let users download apps outside the official store, using a system Apple put in place for businesses and educational institutes to install custom apps without going through the App Store. You must then manually install these apps.
Once the app is up and running, it appears to work like a legitimate crypto wallet. But it isn’t. Instead, it’s stealing the currency deposited into it.
Spelling, icons and description
The first step in ascertaining whether an app is legit is checking out the spelling and icon. Fake apps usually have a name and icon that looks similar to the legitimate one, but something is usually off.
If the app or developer names are misspelled, for example, the software is most likely phony. A quick search about the app on the internet will help to confirm its legitimacy.
It is also important to consider if the app has a Google Editor’s choice badge. The badge is a distinction provided by the Google Play editorial team to recognize developers and apps with outstanding quality. Apps with this badge are unlikely to be fake.
Don’t be a victim
Follow these tips to keep crypto scammers at bay:
- Use official apps from official app stores that contain links to official websites.
- Be wary of online ads for crypto.
- Research any wallet app you’re interested in. Look for reviews and information about the company behind the app.
- Before you buy crypto, read Kim’s eBook on the subject.
Application permissions
Counterfeit apps usually request more permissions than necessary. This ensures that they glean as much data as possible from victims’ devices.
As such, users should be wary of apps that require off-center permissions, such as device administrator privileges. Such authorizations could give cybercriminals unfettered access to a device and allow them to intercept sensitive data that can be used to unlock financial accounts, including crypto wallets.
Intrusive app permissions can be blocked via a phone system’s privacy settings.
Fake websites
Scammers sometimes create fake cryptocurrency trading platforms or fake versions of official crypto wallets to trick unsuspecting victims. These fake websites usually have similar but slightly different domain names from the sites they attempt to mimic. They look very similar to legitimate sites, making it difficult to tell the difference. Fake crypto sites often operate in one of two ways:
- As phishing pages: All the details you enter, such as your crypto wallet’s password and recovery phrase and other financial information, end up in the scammers’ hands.
- As straightforward theft: Initially, the site may allow you to withdraw a small amount of money. As your investments seem to perform well, you might invest more money in the site. However, when you subsequently want to withdraw your money, the site either shuts down or declines the request.
Phishing scams
Crypto phishing scams often target information relating to online wallets. Scammers target crypto wallet private keys, which are required to access funds within the wallet. Their method of working is similar to other phishing attempts and related to the fake websites described above. They send an email to lure recipients to a specially created website asking them to enter private key information. Once the hackers have acquired this information, they steal the cryptocurrency in those wallets.
Pump and dump schemes
This involves a particular coin or token being hyped by fraudsters through an email blast or social media such as Twitter, Facebook, or Telegram. Not wanting to miss out, traders rush to buy the coins, driving up the price. Having succeeded in inflating the price, the scammers then sell their holdings – which causes a crash as the asset’s value sharply declines. This can happen within minutes.
Fake apps
Another common way scammers trick cryptocurrency investors is through fake apps available for download through Google Play and the Apple App Store. Although these fake apps are quickly found and removed, that doesn’t mean the apps aren’t impacting many bottom lines. Thousands of people have downloaded fake cryptocurrency apps.
Fake celebrity endorsements
Crypto scammers sometimes pose as or claim endorsements from celebrities, businesspeople, or influencers to capture the attention of potential targets. Sometimes, this involves selling phantom cryptocurrencies that don’t exist to novice investors. These scams can be sophisticated, involving glossy websites and brochures that appear to show celebrity endorsements from household names such as Elon Musk.
Giveaway scams
This is where scammers promise to match or multiply the cryptocurrency sent to them in what is known as a giveaway scam. Clever messaging from what often looks like a valid social media account can create a sense of legitimacy and spark a sense of urgency. This supposed ‘once-in-a-lifetime’ opportunity can lead people to transfer funds quickly in the hope of an instant return.
Blackmail and extortion scams
Another method scammers use is blackmail. They send emails that claim to have a record of adult websites visited by the user and threaten to expose them unless they share private keys or send cryptocurrency to the scammer.
Cloud mining scams
Cloud mining refers to companies that allow you to rent mining hardware they operate in exchange for a fixed fee and a share of the revenue you will supposedly make. In theory, this allows people to mine remotely without buying expensive mining hardware. However, many cloud mining companies are scams or, at best, ineffective – in that you end up losing money or earning less than was implied.
Fraudulent initial coin offerings (ICOs)
An initial coin offering or ICO is a way for start-up crypto companies to raise money from future users. Typically, customers are promised a discount on the new crypto coins in exchange for sending active cryptocurrencies like bitcoin or another popular cryptocurrency. Several ICOs have turned out to be fraudulent, with criminals going to elaborate lengths to deceive investors, such as renting fake offices and creating high-end marketing materials.
How to spot cryptocurrency scams
So, how to spot a crypto scam? Warning signs to look out for include:
Promises of guaranteed returns: No financial investment can guarantee future returns because investments can go down as well as up. Any crypto offering that promises you will definitely make money is a red flag.
A poor or non-existent whitepaper: Every cryptocurrency should have a whitepaper since this is one of the most critical aspects of an initial coin offering. The whitepaper should explain how the cryptocurrency has been designed and how it will work. If the whitepaper doesn’t make sense – or worse, doesn’t exist – then tread carefully.
Excessive marketing: All businesses promote themselves. But one way that crypto fraudsters attract people is by investing in heavy marketing – online advertising, paid influencers, offline promotion, and so on. This is designed to reach as many people as possible in the shortest time possible – to raise money fast. If you feel that the marketing for a crypto offering seems heavy-handed or makes extravagant claims without backing them up, pause and do further research.
Unnamed team members: With most investment businesses, it should be possible to find out who the key people behind it are. Usually, this means easy-to-find biographies of the people who run the investment plus an active presence on social media. If you can’t find out who is running a cryptocurrency, be cautious.
Free money: Whether in cash or cryptocurrency, any investment opportunity promising free money is likely to be fake.

How to protect yourself from cryptocurrency scams
Many crypto frauds are sophisticated and convincing. Here are some steps you can take to protect yourself:
Protect your wallet: To invest in cryptocurrency, you need a wallet with private keys. If a firm asks you to share your keys to participate in an investment opportunity, it’s highly likely to be a scam. Keep your wallet keys private.
Keep an eye on your wallet app: The first time you transfer money, send only a small amount to confirm the legitimacy of a crypto wallet app. If you’re updating your wallet app and you notice suspicious behavior, terminate the update, and uninstall the app.
Only invest in things you understand: If it’s not clear to you how a particular cryptocurrency works, then it’s best to pause and do further research before you decide whether to invest.
Take your time: Scammers often use high-pressure tactics to get you to invest your money quickly – for example, by promising bonuses or discounts if you participate straightaway. Take your time and carry out your own research before investing any money.
Be wary of social media adverts: Crypto scammers often use social media to promote their fraudulent schemes. They may use unauthorized images of celebrities or high-profile businesspeople to create a sense of legitimacy, or they may promise giveaways or free cash. Maintain a healthy skepticism when you see crypto opportunities promoted on social media and do your due diligence.
Ignore cold calls: If someone contacts you out of the blue to sell you a crypto investment opportunity, it’s probably a scam. Never disclose personal information or transfer money to someone who contacts you in this way.
Only download apps from official platforms: Although fake apps can end up in the Google Play Store or Apple App Store, it is safer to download apps from these platforms than elsewhere.
Do your research: The most popular cryptocurrencies are not scams. But if you haven’t heard of a particular cryptocurrency, research it – see if there is a whitepaper you can read, find out who runs it and how it operates, and look for genuine reviews and testimonials. Look for an up-to-date and credible fake cryptocurrency list to check for scams.
Is it too good to be true: Companies that promise guaranteed returns or to make you rich overnight are likely to be scams. If something seems too good to be true, tread carefully.
Finally, as with any investment opportunity, never invest money you can’t afford to lose. Even if you’re not being scammed, cryptocurrency is volatile and speculative, so it’s essential to understand the risks.
What to do if you fall victim to a crypto scam
Falling victim to a cryptocurrency scam can be devastating, and it’s essential to act quickly if you have made a payment or disclosed personal information.
Contact your bank immediately if you have:
- Made a payment using a debit or credit card.
- Made a payment via bank transfer.
- Shared personal details about yourself.
Crypto fraudsters often sell the details they have captured to other criminals. So, it’s essential to change your usernames and passwords across the board, to prevent further damage. If you are the victim of a social media crypto scam, you can report it to the relevant social media platform. Depending on where you live, you can report frauds to the relevant body in your jurisdiction – for example, in the US, that would be the Federal Trade Commission. Other countries have their own equivalents.
The number of downloads
The number of times that an app has been downloaded is usually an indicator of how popular it is. Apps from reputable developers typically have millions of downloads and thousands of positive reviews.
Inversely, apps with just a few thousand downloads require greater scrutiny.
Confirming authenticity by contacting support
If unsure about an application, contacting support through the company’s official website could help to avoid financial losses due to fraud.
Furthermore, authentic apps can be downloaded from a company’s official website.
Cryptocurrencies are underpinned by relatively new technology, so it is only natural that there are teething problems when it comes to use and adoption. Unfortunately, in recent years, black hats have targeted naïve crypto enthusiasts using fake crypto apps.
While the problem is likely to persist for several years, increased scrutiny by tech companies is likely to temper the issue in the long run.
Literature:
Investigation of Cryptocurrency Wallets on
iOS and Android Mobile Devices for Potential Forensic Artifacts
Angelica Montanez
Summary
This type of fraudulent activity is not only prevalent at the moment, but it is also on the rise. Every day, a growing number of people fall victim to this. Users should always be cautious and suspicious of phishing scams.
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/EkU8YhB91MI
Source: https://cryptodeeptools.ru/crypto-wallet-protection



